Network devices are the building blocks and backbone of today’s contemporary and large-scale networks and systems. The role of network devices is to ensure reliable and efficient transfer, filtering, and management of data across or within networks. Many network devices range from basic layer one hubs or repeaters to layer two switches, layer three routers, load balancers, virtual private networks, and intrusion prevention systems.
Learning Objectives
The room aims to teach techniques for identifying and mitigating security vulnerabilities, hardening network device configurations, and implementing security best practices. By the end of this room, you should be able to assess and strengthen network device security, enhance network resilience, and effectively defend against common cyber threats.Learning Pre-requisites
An understanding of the following topics is recommended before starting the room:
Let’s begin!
Task 2 Common Threat and Attack Vectors
Difference between Network Devices and Endpoint Devices
Before proceeding with our actual topic, it is imperative to understand the difference between network devices and endpoint devices. Endpoint devices refer to any device that can generate or consume data on a network, such as Laptops, Desktops, Smartphones, Tablets, Printers, Servers, and IoT Devices. They are typically located at the edge of a network and interact directly with users. The figure below shows the difference between endpoint and network devices based on their functionality, traffic, and configuration.

Common Threats and Attack Vectors of Network Devices
The unprecedented growth in today’s Information and Communication Technology (ICT) networks has transformed the world into a global village. On the other hand, it has also given rise to multifarious malicious activities by cyber attackers. As we have already studied, the various network devices are the backbone of modern ICT networks. To ensure confidentiality, integrity, and availability (CIA) in our networks and systems, it is imperative that we implement security hardening measures to these devices. Some common goals of hardening include protection from unauthorised access & attacks/exploits, enforcement of access policies, prevention of data theft, and continuous availability of critical systems.
| Threat | Description | Attack Vector |
| Unauthorised access | Gain unauthorised control of a network device, and then the complete network. | Password attacks (brute force, dictionary & hybrid)Exploit known vulnerabilities, e.g. RCESocial Engineering/Phishing attack to trick network administrators into disclosing sensitive information such as usernames and passwords of devices |
| Denial of Service (DoS) | Disruption of critical devices and services to make them unavailable to genuine users. | Flooding devices with fake requestsExploiting vulnerabilities in logical or resource handlingManipulating network packets |
| Man-in-the-Middle Attacks | Intercept the network requests between two parties by masquerading as each other to steal sensitive information or alter/manipulate the requests. | ARP spoofingDNS spoofingRogue access points |
| Privilege escalation | Gaining higher-level privileges or rights to perform restricted actions, e.g. accessing sensitive information or executing malicious code. | Weak passwords or use of the same passwords for user and admin accountsExploiting vulnerabilitiesMisconfigurations |
| Bandwidth theft/ hotlinking | Linking a bandwidth-intensive resource (image or video) from an external website to its original website, without permission. This can cause increased traffic to the original website. | Scraping large volumes of data DoS attacks Malware attacks |

Task 3 Common Hardening Techniques
General Techniques
Hardening techniques are meant to reduce the attack surface of a system or network by removing unnecessary functionality, limiting access, and implementing various security controls. Some standard methods are mentioned below:
- Updating & Patching: Ensuring the latest version of the Operating System and underlying applications of all devices and systems and installing regular security patches is the core hardening measure. Outdated OS and applications contain vulnerabilities that attackers can exploit.
- Disabling unnecessary services & ports: Turn off all unnecessary services and block all ports (physical and virtual) that are not needed for system functionality. This will reduce the attack surface by minimising the number of entry points an attacker can exploit.
- Principle of Least Privilege (POLP): Restrict users and processes to only the minimum necessary permissions required to perform their functions.
- Logs Monitoring: Implement a log monitoring system to monitor for unusual activity or security events.
- Backup regularly: Take routine backups of systems and configurations as they can help recover from a security incident or system failure.
- Enforcing Strong Passwords: Change default login passwords and use strong passwords that are at least ten characters long with a combination of small letters, capital letters, special characters, and numbers. These types of passwords protect against dictionary and brute-force attacks.
- Multi-Factor Authentication (MFA): MFA is an additional security layer requiring two or more types of identification before accessing the account or system. The two factors are generally something we know (like passwords) and something we have (like biometrics).
Importance of Secure Protocols
Secure protocols play a critical role in network device hardening by protecting against unauthorised access and data breaches. They ensure that sensitive data transmitted between devices is encrypted and cannot be intercepted by malicious actors. Moreover, secure protocols also help prevent man-in-the-middle attacks and other network-based exploits. Using secure protocols, network administrators can ensure that only authorised personnel can access sensitive information and perform system administration tasks. Necessary security protocols include HTTPS, SSH, SSL/TLS, and IPsec. You can learn more about secure network protocols in this room.
Removal/Blocking of Insecure Protocols
In addition to using secure protocols, removing and blocking access to those insecure protocols is equally essential, which will decrease an attacker’s attack surface. Most important are the protocols that transmit data in clear text without encrypting them, like FTP, HTTP, Telnet, SMTP, and more. Moreover, there are inherently secure protocols (e.g. LDAP, RDP, SIPS); however, they can allow attackers to exploit the network if configured incorrectly.
Implementation of Monitoring and Logging Controls
Logging in network devices is essential for detecting and investigating security incidents, identifying performance issues, and complying with regulatory requirements. It provides a record of events and activities on the device, which can be used for troubleshooting, forensic analysis, and auditing purposes. The following techniques are generally used for logging:
- Syslog: A protocol to standardise the transfer of log messages, with the purpose of storing and analysing log messages to a central server.
- SNMP: Traps a notification sent by a network device to a management system when a predefined event occurs.
- NetFlow: A protocol used to collect and analyse network traffic data for monitoring and security analysis.
- Packet Captures: Capturing network traffic and storing it for analysis using a tool like Wireshark.

Task 4 Hardening Virtual Private Networks
Virtual private networks (VPNs) are now needed in the age of remote work and online communication to protect sensitive data and preserve privacy. Yet, hardening VPNs is crucial to ensure their efficiency as cyberattacks continue to develop. Hardening VPNs entails adopting additional security measures, such as multi-factor authentication and encryption techniques, to make it more challenging for hackers to access the network. By taking these extra precautions, businesses can better safeguard their data and defend against cyberattacks, raising their security level and bringing them more peace of mind.

This task will cover hardening a VPN server by focusing on secure authentication, strong encryption, and proper update. We cover the different configuration options available and which are considered the safest by the industry.
Connecting to the Machine
We will be using an Ubuntu machine with OpenVPN installed throughout the room. You can start the virtual machine by clicking Start Machine. The machine will start in a split-screen view. In case the VM is not visible, use the blue Show Split View button at the top-right of the page. Please wait 3-5 minutes to make sure the VM is fully booted.
Standard Hardening Practices
Usually, all the VPN servers consist of server-side and client-side configurations through a standard config file. System administrators must understand the file’s content and edit it as per best security practices. You will be using the following commands in the upcoming exercises:
- The OpenVPN server config file is located at
/etc/openvpn/server/server.conf. Once the machine is loaded, open the terminal and load the file by issuing the commandsudo nano /etc/openvpn/server/server.conf. - Once you made the desired changes in the file, press
Ctrl+Oand hitEnter, then pressCtrl+Xto exit. - The command
sudo systemctl restart openvpn-server@server.servicecan restart the OpenVPN service.
Moving forward, the following are some of the significant hardening practices for a VPN server:
- Use strong encryption algorithm: Configure the VPN gateway to use strong encryption to protect data in transit. The cipher directive in the config file can be used to select the encryption scheme. The possible options for cipher include AES, Blowfish, Camellia, and more. For example, AES-128-CBC mode means to use the AES encryption algorithm with a key size of 128-bit in Cipher Block Chaining (CBC) mode, as seen below. AES-256-CBC is typically considered one of the strongest cipher encryption nowadays.
- Keep VPN gateway software up-to-date: Ensure that the VPN gateway software is always updated with the latest security patches and updates. Every VPN software has a different method for it. You can use
sudo apt upgrade openvpnto update OpenVPN (please note that the attached VM does not have an internet connection). - Implement strong authentication: Use strong authentication mechanisms such as a combination of Transport Layer Security (TLS) and a secure hashing algorithm. We can use the
authdirective to specify the exact algorithm in the OpenVPN configuration file to ensure that a secure hashing algorithm will be used for packet authentication. Some of the options for auth directive are SHA1, SHA128, SHA256, SHA512 and MD5. You can set the auth directive through the following command: - Change default settings: Change the default usernames and passwords to something unique to reduce the risk of unauthorised access to the VPN gateway.
- Enable Perfect Forward Secrecy (PFS): Perfect Forward Secrecy (PFS) in OpenVPN generates unique session keys for each session to strengthen the security of the VPN connection. Because of this, even if a hacker successfully obtained a session key, they could not use it to decode more sessions. For each session, PFS generates a new set of encryption keys, preventing the possibility of remotely decrypting previously acquired material. As a result, it is far more challenging for an attacker to spoof the VPN connection and steal sensitive data. We can use the
tls-cryptdirective in the OpenVPN configuration file to enable PFS. Thetls-cryptdirective requires a key that can be generated using the commandsudo openvpn --genkey --secret my.keyand should be placed in the same directory on the server. Choosing the appropriate cipher and auth, like cipher AES-256-CBC and auth SHA 256, supports PFS if combined with tls-crypt. The exact configuration is mentioned below: - Dedicated Users for VPN Server: Limit user access by creating a dedicated user account and group with restricted permissions specifically for running the OpenVPN server.
Plenty of other options can help you secure and harden an OpenVPN server; it all depends on the organisation’s requirements. However, by default providing restricted access to the users enables a limited attack surface for the attacker.

Task 5 Hardening Routers, Switches & Firewalls
Routers and switches must be hardened for the network infrastructure to be secure and reliable. Every network needs routers and switches, often the first line of defence against potential security risks and attacks. By hardening these devices, we can lower the possibility of unauthorised access, avoid data breaches, and ensure network service availability. Improved network performance, increased resilience against cyberattacks, and regulatory compliance are a few of the main advantages of hardening routers and switches. Routers and switches without enough hardening are susceptible to various attacks, including denial of service and network profiling.
In the previous task, we studied how to harden a network device using a configuration file on a Command Line Interface (CLI). In this task, we will use the web interface to learn different methods for hardening a router. We will be using a router that has OpenWrt installed, which is a free and open-source Linux-based operating system for embedded devices. We know that a router configuration varies from product to product; however, a few standard techniques can be applied to protect from potential attacks. You can access the OpenWrt web interface at MACHINE_IP:8080 with the following credentials:
- Username:
root - Password:
TryHackMe
Recommended Hardening Techniques
- Setting up the device: While setting up any network device, it is necessary to fill in all relevant details like hostname, timezone, logging, and more. These features assist in conducting incident handling in case of a compromise. For example, logging must be enabled to log all the events with the default alert level
Debug. Similarly, timezone and time synchronisation must be set accurately to properly correlate events with their occurrence time. You can enable and modify these settings throughSystem > Systemand select the desired option.

- Change default credentials: Usually, the admin web interface is protected through a username and password, and people tend to ignore changing the default. A threat actor can access the router’s admin interface and compromise the whole network using default credentials. We can change the default password in OpenWrt through
System > Administration, enter a new password, and click theSavebutton.

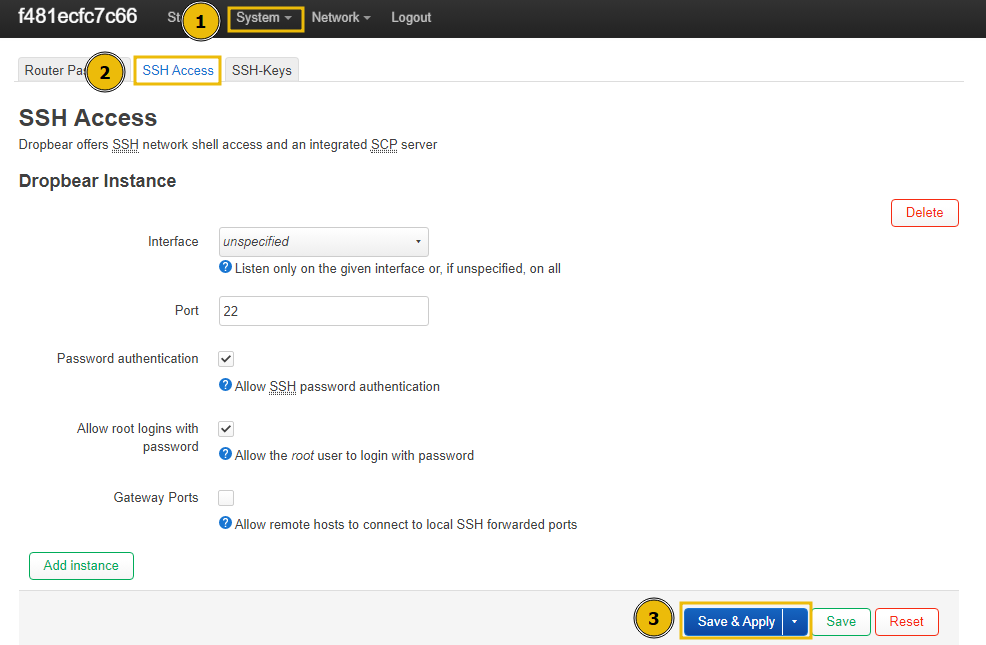
- Enable secure network protocols: For a network device to maintain the confidentiality, integrity, and availability of network traffic, secure protocols must be enabled. Secure protocols like HTTPS, SSH, and SSL/TLS offer encrypted authentication mechanisms and communications to stop unauthorised access and eavesdropping. By enabling secure protocols on a router, you can reduce the risk of data breaches, man-in-the-middle attacks, and other security threats. You can enable SSH in OpenWrt through
System > Administration > SSH Access, then select the interface and port number and clickSave & Apply. Moreover, you can also add specific public SSH-Keys for passwordless login.
- Disabling unnecessary scripts: Almost every network device executes some startup scripts to provide a better user experience to a user. For example, crontab is executed on startup to verify and execute any cron job. Threat actors try to gain persistent access on a network device by adding their malicious scripts on the startup. We can add/remove startup scripts and set the priority through
System > Startup.

- Securing Wi-Fi: If the router has Wi-Fi capabilities, securing the Wi-Fi by enabling strong encryption like WPA2/WPA3, disabling SSID broadcast, changing default passwords, and more.

Task 6 Hardening Routers, Switches & Firewalls – More Techniques
Recommended Hardening Techniques
- Manage traffic rules: Network devices allow you to create and implement traffic rules that accept/deny network traffic. For example, we notice that the data of users connected with our network device is being exfiltrated to a command and control server IP address. We can create a rule to block all traffic where the destination IP matches the attacker’s command and control server. We can add/edit traffic rules through
Network > Firewall > Traffic Rules, and clickAddto create a new rule.

- Monitor traffic: As a network administrator, keeping track of network traffic, like uploads and downloads of data at different intervals, is essential. For example, you have excessive data uploaded from one of the email servers to an unknown IP address. Such alerts enable you to take remedial measures and stop data pilferage timely. Usually, network devices provide real-time graphs to monitor the traffic. We can view real-time traffic statistics through
Status > Realtime Graph > Traffic.

Note: Since no client is connected with the network device, you won’t see any traffic in the real-time traffic statistics on the target machine.
- Configuring port forwarding: A firewall’s port forwarding capability enables inbound traffic from the internet or other sources to be routed to a particular device or service on the internal network. The firewall can send incoming traffic to the appropriate device or service on the internal network by establishing port forwarding rules while blocking any other incoming traffic that does not comply with the rules. This feature helps host applications that need outside access, granting remote control of internal devices. Port forwarding should be used carefully because it can expose internal devices and services to potential security issues if improperly secured and configured. Threat actors could add new rules here for creating connections to external command and control servers. We can configure port forwarding through
Network > Firewall > Port Forwards, and click theAddbutton.

- Monitoring scheduled tasks: It is important to monitor scheduled tasks to confirm that the original scheduled tasks lists are not modified by a threat actor. To add or remove scheduled tasks, which in our case are handled by cron, navigate to
System > Scheduled Tasks, add the new cron job, and clickSave. You can learn how to create cron jobs here.

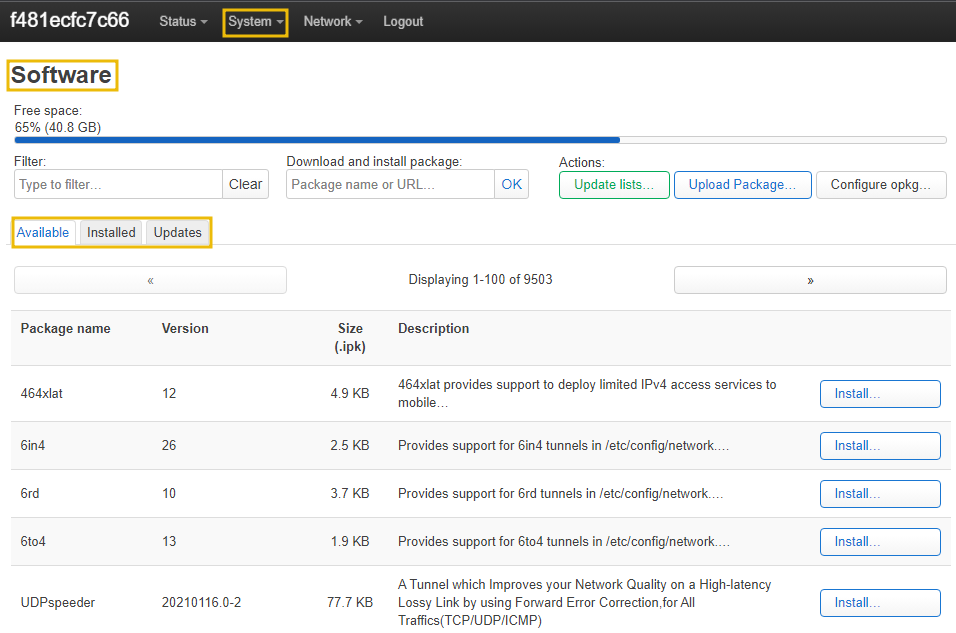
- Update firmware: It is essential to update the firmware and installed packages on a regular basis to avoid any know/unknown attacks. We can update the firmware through
System > Software.
Additional Techniques in an Enterprise Environment
A network device deployed in an enterprise environment generally provides an increased attack surface for an attacker to launch attacks. As enterprise environments include a variety of devices with different models, makes, and types, there are no definite rules to harden network devices; however, a few important ones are mentioned below:
- Configuring port security: This includes limiting the number of MAC addresses registered on a switch port and taking particular action whenever unauthorised access is detected. Enabling port security enables an administrator that data is coming from a valid source and will be forwarded to a legitimate receiver.
- Preventing ARP spoofing: ARP spoofing is one of the most common vectors for launching man-in-the-middle attacks on the network. The threat can be mitigated by enabling static ARP tables and implementing MAC address filtering. You can learn more about mitigating ARP spoofing here.
- Preventing rogue DHCP servers: The attacker creates a spoofed DHCP server that can be later on used for assigning IPs to clients and launching MITM attacks. Mitigation measures to prevent such attacks include configuring static DHCP binding and ensuring no unknown devices are added to a network through network mapping tools. You can learn more about DHCP here.
- Enabling IPv6: Unlike IPv4, IPv6 has built-in support of IPsec that can be used to secure network communication and provide confidentiality, integrity, and authenticity. Moreover, this will help in protection against MITM, eavesdropping, and tampering of packets in transit.
A network device is configured with many options for protection against cyberattacks. We have discussed some of the most common and important ones in this task.

Task 7 Important Tools for Network Monitoring
Network monitoring tools are enablers for maintaining the security and performance of networks. These tools use sophisticated algorithms and protocols to capture and analyse real-time network traffic. In addition, they enable network administrators to detect and troubleshoot problems such as bandwidth bottlenecks, network outages, and security threats. Some commonly used tools and their usage is mentioned below:
| Tool | Usage Description |
| Nagios | A popular open-source software for monitoring systems, networks, and infrastructure. It provides real-time monitoring and alerting for various services and applications. |
| SolarWinds Network Performance Monitor | A comprehensive network monitoring tool that provides real-time visibility into network performance and availability. It includes network mapping, automated network discovery, and customisable dashboards. |
| PRTG | An all-in-one network monitoring tool that provides comprehensive performance and availability monitoring. It includes real-time traffic analysis, custom dashboards, and customisable alerts. |
| Zabbix | A powerful open-source network monitoring tool that provides real-time network performance and availability monitoring. It includes features such as customisable dashboards, network mapping, and alerting. |

In conclusion, network devices are fundamental in today’s modern computer networks. As we have studied, these devices form the backbone of networks, and their hardening is essential for maintaining the security and performance of these networks.
Hardening involves implementing various security measures such as firmware updates, change of default passwords, strong authentication mechanisms, encryption, logging, and secure protocols. By following best practices for network device hardening, network administrators can significantly reduce the risk of security breaches, data loss, and network downtime.
In addition, we have also studied the importance of network monitoring tools; they can provide real-time visibility into network performance and detect potential security threats. The key takeaway from this room is that organisations must prioritise network device hardening as a fundamental aspect of their overall cyber security strategy to protect their infrastructure from cyber attacks.
Leave a Reply