Introduction
In this tab, we can find several useful options that are invaluable in any bugbounty hunters toolbelt in my opinion. I’m not going to bore you with the very basics, i assume you already know those. Instead i am going to show you all the cool tricks we can with this section of burp.
Site map
The site map displays any URL that we visited while browsing the website manually if we have our passive crawling job active in the background to fill the site map.
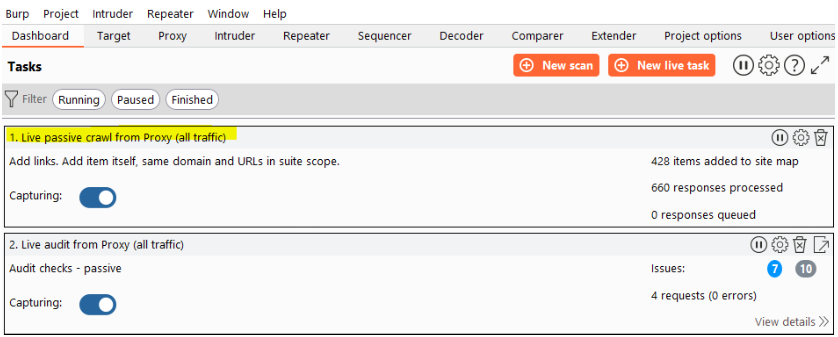
One thing i will always do is sort my responses via status code. This makes it easier to view the requests that return a 200 status code and then i can judge if they should.
Please note that by default items with a response code of 4xx (i.e. 403 are not shown in the site tree. We can enable those in the filtering, that’s where the real fun starts.
filtering
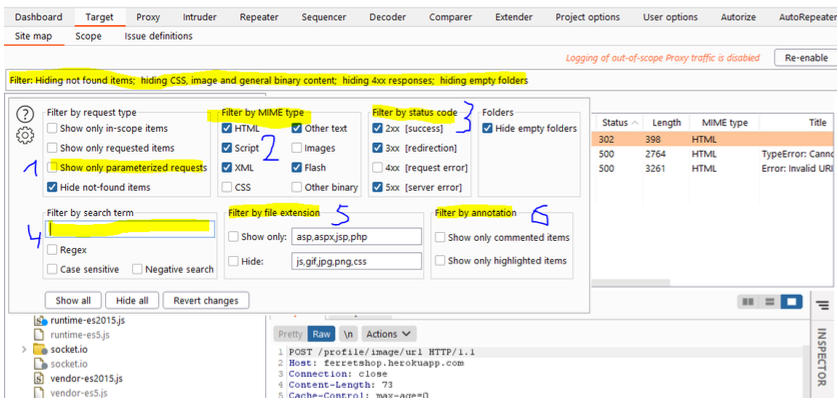
If we click the filter bar at the top of the screen, we can some very useful filters.
Showing only the paramterised requests will show us all the requests that allow us some kind of interaction with the server. These are the requests that i care about mosts as they talk to the API.
Filtering by mime type allows us to include or exclude certain types of files such as scripts or CSS files by checking or unchecking the checkbox respectively.
If we want to show or hide certain status codes, that’s also possible like the 4xx status codes which are disabled by default
If we want to search for specific terms, that also possible. We can do this in negative search as well, which would mean that we would exclude requests with the search term in it.
If we want to hide or show certain file types, that’s also possible but we can’t use both together as they would cancel eachother out
We can also annote or comment certain requests by right clicking them in the site map, repeater or proxy history and then we can filter on those requests.
Scope
insignifficant section is the most important one of our whole project. If we don’t In here, we set our scope as the name says it might not seem like it, but this 🙂
set our scope properly we risk of testing targets which are not covered in our don’t like all the hacker attention.
program. These targets can be neferious but they can also be 3rd parties which
On the other hand, set the scope wrong or too strict and you are missing a ton of potential requests.
Hackerone has configuration files for burp you can download.
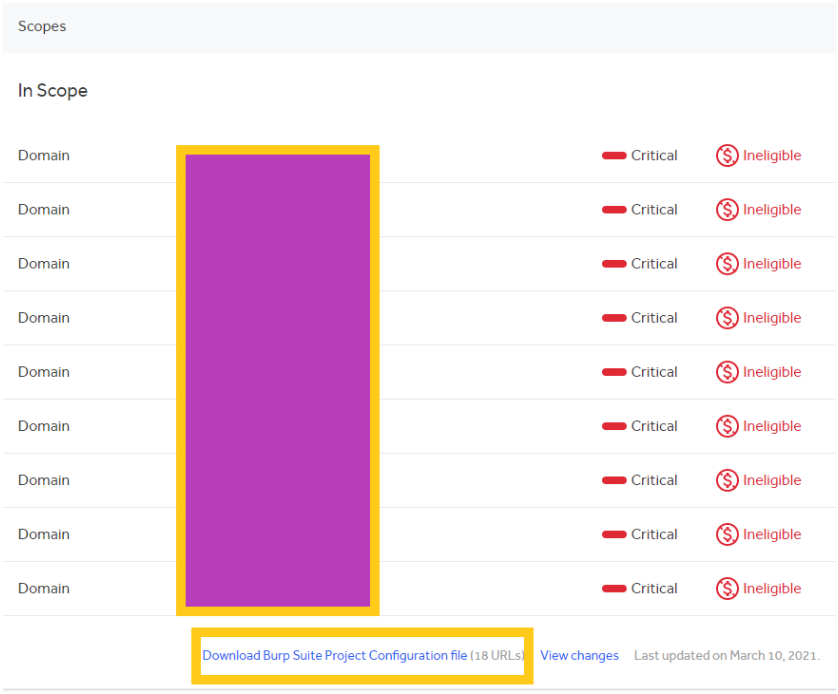
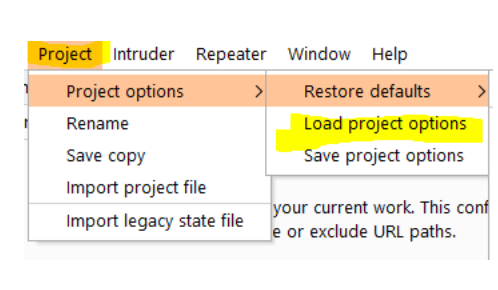
You can then import this file via the project options import functionality under
“Project > Project options > Load Project options”
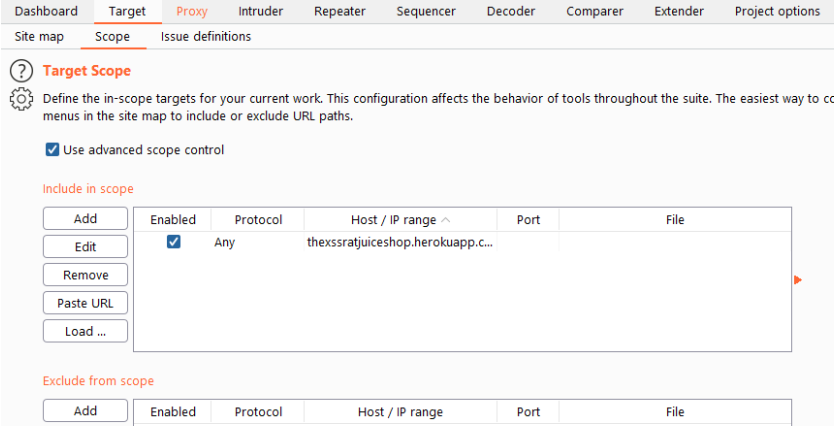
I always use the “Advanced scope control” myself which allows you to enter regular expressions. Make sure you don’t include the protocol HTTPS// or HTTP//) in the host or ip range as that is a seperate field.
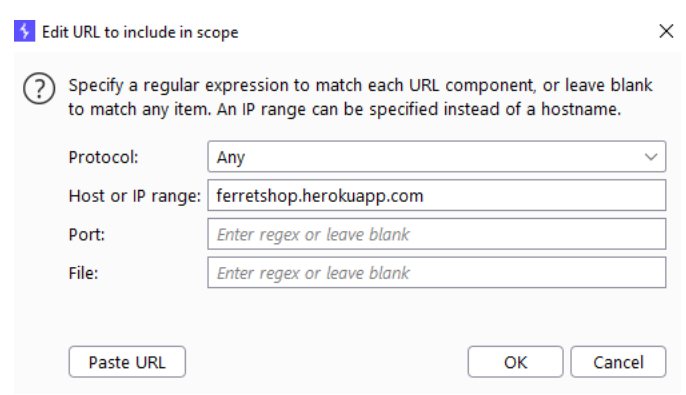
Make note of the fact that you can also exclude URLs from the scope. This can be very useful if you have certain subdirectories for example that are out of scope or if you are at an assignment that only provides out of scope URLs and a *.target.com in scope URL.
Issue definitions
This is just a list of all issues that can be detected by burp and their descriptions.
Leave a Reply